
Regional expansion of ScanSnap Cloud – the service enabling PC-less scanning for increased efficiency at work and in the house.
April 2, 2020
LexisNexis Australia – Technology Integrations
April 2, 2020Buyers Beware: Scamming Is Rife, Especially In a Time of Crisis
For years, scammers have been using a combination of Blackhat SEO techniques, phishing sites and newsworthy events to either trick individuals into giving up personal information including credit card numbers or to install malware or both. Preying on an individual’s fears has always been a go to tactic for scammers.
Recently a friend texted me and asked if I could take a look at a website his wife used to try and buy some 3M N95 face masks from. He was concerned that the site did not appear to be legitimate. “Sure”, I said, “What is the domain?” He sent it over. mygoodmask[.]com. Having spent the last decade looking at malware, spammers and scammers, I responded immediately, “Yes, it’s very bad. Tell her to cancel her credit card as soon as possible.”
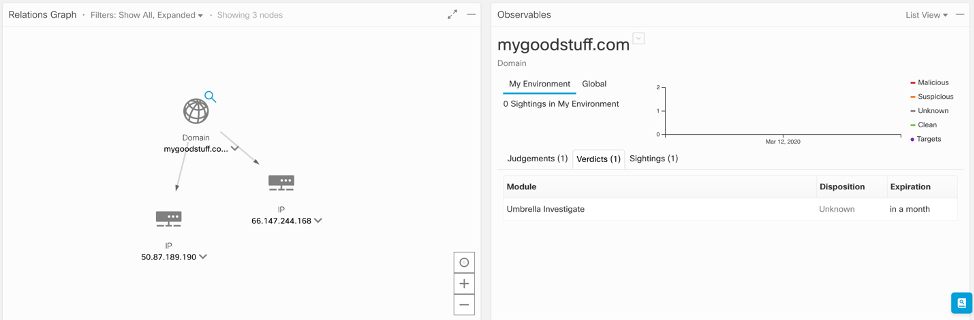
I figured I’d take a closer look at the domain to confirm if I was right. Dropping the domain into Cisco Threat Response – our platform that accelerates investigations by automating and aggregating threat intelligence and data across your security infrastructure. Threat Response didn’t return anything useful aside from the IP Addresses it resolved to. Since the platform is configured for my test organization at the office, it’s not going to show me any hosts that may have visited that domain, but it is still a great source of intelligence. It showed that Cisco was aware of the domain, but there was no additional information – not surprising for newly created and used domains. There is more than one way to determine if a domain is suspicious.
Enriching the two IP addresses, 50[.]97.189.190 and 66[.]147.244.168, returned everything I needed to decide that the original site was malicious. Nearly two hundred domains resolving to those two addresses, none of which looked like ones I’d like to end up on.
At this point I was curious about the website itself and wanted to take a closer look. I submitted the domain to Threat Grid, Cisco’s malware analysis tool. It immediately redirected to greatmasks[.]com which resolved to 37[.]72.184.5. Using Glovebox, a capability in Threat Grid that allows full interaction with the virtual machine, I attempted to buy some masks from the website. I used an expired card number to purchase my masks. They are using PayPal to collect payments and validate card numbers.
The results produced from the analysis highlighted further details on the website, indicating a high level of suspicious activity.
Drilling down on the IP address that the new domain resolved to, we found another related domain, safetysmask[.]com. At this point it would be easy to create a new Casebook and add these observables to the investigation.
For me, one of the most telling signs of an unknown domain is the lookup frequency and activity mapped to the domain creation date and DNS changes. A scammer may register domains and park them until they’re ready to use them. At that point they’ll set up a website and point that domain to an IP.
Looking at the timeline and domain lookup activity in Cisco Umbrella, our DNS-layer SaaS solution, it’s clear that this website has been up for less than a month which is unusual, especially in context of this investigation.
Using a combination of our platform capability and our DNS-layer security, I was able to validate that this domain, IP Addresses, and related domains were malicious. With investigations of this nature, the domain or IP might not always have a known disposition at a certain point in time but often, by following the breadcrumb trail of related information, it’s easy to make a determination and judgement about the original domain. Another path to determining the disposition of these domains is to drill down into the observables in Umbrella.
Cisco Security products not only integrate via Threat Response, there are multiple direct integrations between products as well. These integrations are used to share threat intelligence produced by individual products and to share capabilities across products through API integrations, data visualization and cross product capabilities such as Casebook’s browser plugin.
Umbrella, our cloud-delivered DNS- layer of protection, integrates with Threat Grid, our malware analysis tool, and this allows Umbrella to show information produced through dynamic analysis, mapping domains and IP addresses to samples seen in Threat Grid’s global database, providing another method of determining disposition.
By the end of my digging, I had found hundreds of scams related to sports events, fashion accessories, flu season and more. All easily searchable within your organization via Threat Response and just as easily blocked via Umbrella.
What began as just a way to help a friend one evening, became a quick but comprehensive investigation into how bad actors are trying to capitalize on a global health crisis. Hopefully this was helpful in showing how easy it can be to validate the disposition of a domain using related observables, and in doing so, build out a collection of new content to be leveraged in your environment for detection and prevention. Writing this up took longer than the investigation itself. 
Note to readers:
If you’re using Threat Response and Umbrella, you’ll be able to reproduce this investigation using the original domain and the domains and IP found in Threat Grid’s analysis of the website.
Dean used the following in his investigation:
- Cisco Threat Response: cisco.com/go/threatresponse
- Cisco Umbrella: cisco.umbrella.com/
- Cisco Threat Grid: cisco.com/go/threatgrid
The post Buyers Beware: Scamming Is Rife, Especially In a Time of Crisis appeared first on Cisco Blogs.











