
Snort 3 Anywhere
December 4, 2021
Presenting the Security Outcomes Study, Volume 2
December 7, 2021How to Build an Integrated Security Posture Using XDR
Digital attacks grew in both volume and sophistication in 2020. As reported by PR Newswire, the number of complaints received by the FBI’s Cyber Division numbered as many as 4,000 a day during the first half of 2020—400% more than it was in the first few months of that year. (Interpol warned of an “alarming rate of cyberattacks aimed at major corporations, governments, and critical infrastructure” around that same time, as noted by ABC News.) Simultaneously, Help Net Security covered a survey where 84% of U.S. respondents indicated that digital attacks had become more sophisticated between mid-2019 and July of the following year.
Many organizations today need to integrate their technologies so that their data doesn’t exist in silos. By knocking down the barriers of disparate data, threats are quickly detected by combining multiple sources of intelligence from across their entire network. Otherwise, they will likely struggle to keep up with attacks that grow in volume and sophistication. The solution: extended threat detection and response (XDR). This security approach helps to reduce incident response time by accelerating threat detection and automating organizations’ responses across their cloud deployments, applications, and other IT assets. Doing so enables them to achieve comprehensive visibility while avoiding a deluge of false positives that can sometimes accompany other security solutions.
Growing Focus on Security Integrations
In that sense, XDR encapsulates organizations’ growing focus on integrating their networking and security technologies. Integration is something that weighs on the minds of many security leaders around the world. For instance, in a 2021 survey covered by Help Net Security, 93% of security heads indicated they’re concerned about the lack of integration between network security platforms and their IT infrastructure. Half of the respondents stated that they’re in the process of looking for open API integrations.
How do organizations integrate multiple products in their environments together and implement a holistic approach like XDR effectively? They might have a lack of expertise on how to do this, after all. If they tried it on their own, some might end up missing something and creating a security gap that a malicious actor could exploit. They could also fail to make an integration that saves them time and resources. So, how can organizations proceed?
Secure Orchestration Workflow Spotlight: “Firewall Impact Red”
Cisco SecureX takes the pain out of integration by connecting the different vendor products in your security environment together to improve overall security posture and have more visibility. It is built-in to any Cisco Security product that you purchase at no additional cost.
SecureX Orchestration is one of the key features. It allows you to use prebuilt and custom playbooks to automate responses, reduce mean time to respond, and eliminate repetitive tasks. You can even integrate third-party products into the workflow.
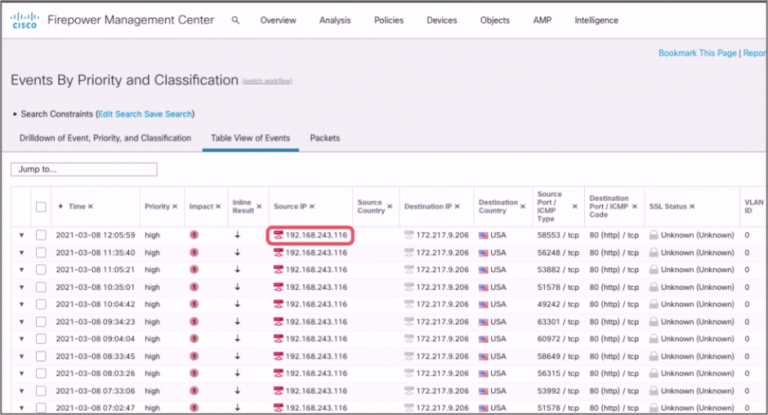
This workflow takes “Impact Red” alerts from Cisco Secure Firewall and searches throughout the rest of your security ecosystem to ensure you’re covered.

Some of the actions that you can take automatically:
- Isolate the host on Cisco Secure Endpoint
- Add the IP to a Custom Detection List on Cisco Secure Endpoint
- Take a Forensic Snapshot using Cisco Secure Endpoint’s Orbital Advanced Search capability
- Block the relevant domains / IPs on Cisco Umbrella
- Move the logged-in user to a deny list on Duo
- Post an alert message on WebEx Teams
- Trigger a ticket in ServiceNow

Of course, you don’t have to integrate all of these, but we’ve already built out the workflow so you can pick and choose what you find most beneficial and show how powerful it can be to have your security environment operate in an integrated fashion.
One integration to highlight is with Cisco Secure Endpoint. Remediation for network-borne threats happen at the endpoint because it is the last line of defense and closest to the source. Using this workflow, Firewall Analysts can respond much more efficiently to security threats sourced at the Firewall, automatically blocking malicious SHAs and isolating the endpoint as needed.
To watch one of our Technical Marketing Engineers talk through the use case and some of the possibilities, see the video below.

This is just one of the many pre-built SecureX Orchestration workflows we’ve come up with to help you automate more tasks in your security environment. Hope you enjoyed this article!
To learn more about how to configure the workflow, visit https://ciscosecurity.github.io/sxo-05-security-workflows/workflows/secure-firewall/0013-impact-red-remediation
Learn more about Cisco Security: https://www.cisco.com/c/en/us/products/security/index.html
We’d love to hear what you think. Ask a Question, Comment Below, and Stay Connected with Cisco Secure on social!
Cisco Secure Social Channels

