Why Endpoint Security Matters in Protecting Remote Workers – Part 2
September 22, 2020
Autodesk Joins Open Design Alliance to Fast Track Improvements to Interoperability
September 23, 2020Are you ready to place a call for simplified cybersecurity? It’s time to stop switchboarding.
My grandfather was born in the 1930s. In the early 2000s, he used to recollect childhood memories of his experience with the telephone while growing up in India. Since the 1990s, advances in this industry have made communication a piece of cake. He would often tell us stories about day trips for the sole purpose of making a phone call, the community experience of the party lines, and bantering with the switchboard operators before he began the conversation – the one he planned to have in the first place.
Pretty much everyone can conjure up a visual from an old movie or TV show of a human operator plugging patch cables into an enormous switchboard for processing phone calls. It’s not cliché to say that telecommunications involve one of the most complex systems fueled by innovation in technology. From a radical way of manually enabling individuals to talk in real-time to becoming automated exchanges with global scale, the industry has evolved to keep up with the consumer.
So, what’s my point with all of this? Let’s back up and look at how security has evolved. In the security landscape, it should come as no surprise that the average company uses 25+ security tools per enterprise environment. Unfortunately, the proliferation of new solutions does more to undermine effective risk management than support it. Your team is still investing time like the human switchboard operators connecting technologies, people, and processes. Burdening teams with even more tools and methodologies only exacerbates the problem, but there’s often no clear alternative.
A call for simplicity
Organizations have done their best to integrate a functioning security infrastructure, but incompatible interfaces, steep learning curves, and siloed communication impede productivity. Making these systems work together is a constant struggle that requires hard-to-find expertise.
For decades, organizations have fought against a shortage of security experts, a talent gap that leaves their teams overworked, overwhelmed, and exhausted. Most started adopting SIEM (Security Incident and Event Management) solutions for general visibility, monitoring, and compliance use cases. Over some time, many organizations have sought vendors that have started including localized built-in orchestration and automation features in a single product. Others have offered SOAR (Security Orchestration, Automation and Response) technology that required significant customization to realize value. The much newer XDR (Extended Detection and Response) approaches are usually backed by an extensive portfolio of products and have unified security incident detection and response. But most XDR platforms still lack the openness to integrate beyond their key partner ecosystem. To complicate things further, these technologies have a longer lead time for implementation and require significant upfront DevSecOps investment.
You are wondering “now what?” Isn’t it time for the security industry to stop switchboarding?
At Cisco, we are doing that with SecureX‑ a cloud-native, built-in platform experience that is integrated and open for simplicity, unified in one location for visibility, and maximizes operational efficiency. The time savings and better collaboration involved with orchestrating and automating security across SecOps, ITOps, and NetOps teams help you build efficiency.
When things don’t work together, skilled people and solid processes have to fill the gaps. How can you make security more efficient for your teams?
Maximize operational efficiency
Following convoluted, manual, and outdated workflows exposes your business to the risk of threats and human error. Do vendors’ API changes break your automation scripts? Does your team need to constantly maintain the bridges between your products?
Automating critical security workflows frees up your teams across the full lifecycle to go from discovering an alert to taking a response action quickly. And by moving faster and doing more with smarter security, you can leverage talent to build a security program that meets your evolving needs instead of making up for the gaps in technology orchestration.

SecureX offers:
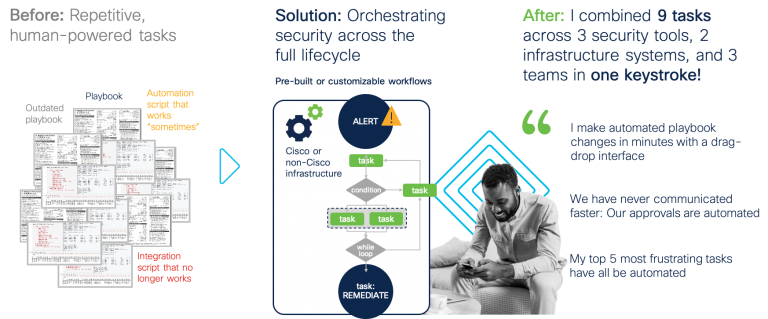
- Multi-domain orchestration: The platform includes full multi-domain orchestration with a no/low-code approach and intuitive drag-drop canvas to deliver a high-performance, scalable playbook automation capability. SecureX’s turnkey interoperability across security, networking, cloud, collaboration, and data center technologies enables expert-free orchestration.

-
- Playbook automation: SecureX will enable you save time and effort associated with automating playbook, and your teams can also develop custom workflows tailored to their environment of Cisco and non-Cisco products. The SecureX threat response application extracts observables, determines the verdict, hunts for targets involved and allows you to take response actions without switching interfaces. SecureX orchestration enables you to build playbooks that can initiate approval workflows to take mitigation and/or preventative actions such as isolating the endpoint targets involved, blocking the malicious domain as necessary, etc.
Want to further your knowledge about the different components of SecureX orchestration? Explore our video series.
For example: Simplify threat hunting by automatically extracting new observables from threat blogs or RSS feeds that SecOps read, enrich with sightings of observables across the environment, create a new case, and start a chat room. Imagine automating more than 8 activities across 23 distinct elements of your security ecosystem that translates into more than 100 hours freed up to improve your posture while minimizing human error.
-
-
- Strengthen your SOC with Cisco Customer Experience (CX) services: Automating common playbooks and queries helps your SOC team focus on investigating and analyzing threats. With SecureX, you gain the ability to build custom workflows across Cisco and multi-vendor solutions. By partnering with our security experts, you ensure that any custom automation work is specifically tailored to your needs and outcomes so you can accelerate your success with CX services for SecureX.
-
Check out these Threatwise TV SecureX episodes to explore the potential use cases.
Reimagine the firewall (15:05)
See Cisco NGFW with SecureX automate rapid alerting, investigation, and response.
Simplify threat hunting (12:45)
Watch how SecureX with Cisco Talos and third-party vulnerability sources simplify the hunt.
Secure remote workers (7:28)
Experience how SecureX scales secure remote access by optimizing VPN capacity.
Next steps: Getting started with SecureX
And there you have it: Get meaningful visibility and maximize efficiency to realize desired outcomes while lowering overhead with SecureX. And stop switchboarding!
If you are new to Cisco, explore our portfolio to start a trial. And if you are already a customer and want to learn more? Watch a 4:36min SecureX demo
The post Are you ready to place a call for simplified cybersecurity? It’s time to stop switchboarding. appeared first on Cisco Blogs.

