Cisco and IBM: Solving Customer Challenges through the Power of Partnerships
December 18, 2019
Anomaly Detection in Complex Systems: Zero Trust for the Workplace
December 20, 2019Combat Modern Day Plague in Security with Email Security and Cisco Threat Response Integration
In January 1900, the four-masted steamship S.S. Australia laid anchor in the Port of San Francisco. The ship sailed between Honolulu and San Francisco regularly, and its passengers and crew were declared clean. However, it is difficult to define what ‘clean’ was in the absence of parameters that could trace the infection back to a single vector. Health and medical professionals struggled to assess and eradicate the disease-make sense of where it came from, if the disease had been seen somewhere in the world, who was the patient zero?
Fast forward to the future, the US Department of Energy’s laboratory Oak Ridge National Lab shuts down the Internet and email services after a cyberattack. The attacks were launched through phishing emails that were sent to about 573 lab employees. The emails were disguised to appear like it came from the lab’s HR department and purported to inform employees of some benefits related changes. Time is of essence in scenarios like this where technology needs to step up to provide answer and not alerts. Is your security program equipped to answer questions-Which email messages have seen this filename or file hash? Which email messages were targeted by this sender email address? Which email messages has seen this subject?
It’s not a matter of IF, but only a matter of when.
The launch of Cisco Threat Response represented a giant leap forward for the goal of reducing or eliminating the burden that exists within today’s Security Operations Center (SOC) by integrating security architecture. The next step in that process was establishing an integration with Security. With solutions like AMP Unity, we have visibility into the email gateway. But Cisco Email Security is the first platform integration that provides deep visibility into content as it travels the network toward the endpoint much like our four-masted steamship. It enables you to find your patient zero!
Being Prepared for the Inevitable
For today’s organizations, email is not only a critical component of business communication, but also a leading attack vector for security breaches. According to Cisco’s Annual Cybersecurity Report, bad actors continue to utilize email as the primary vector for spreading malware.
Additionally, research from the Department of Digital, Culture, Media & Sport states that 80% of businesses with a cybersecurity breach or attack in the last 12 months were targeted by a phishing attack. According to the 2018 Duo Trusted Access Report, 62% of phishing simulation campaigns ran through the Duo Insight tool captured at least one set of user credentials. Nearly a quarter of the campaign recipients clicked the phishing link in the email, and half of those that clicked the phishing link then entered credentials into the fake website. While these attacks aren’t always sophisticated, they are clearly becoming harder to spot by the untrained eye, as hackers find new ways to make malicious emails appear legitimate.
A recent report from Cisco Talos Intelligence Group shared information about a ransomware attack known as LockerGoga that leverages an encryption process to remove the victim’s ability to access files and other data that may be stored on infected systems. Phishing user credentials is one way that an attacker can gain network access, restrict file access, and then deliver a ransom note demanding payment in exchange for keys to decrypt files that LockerGoga has impacted. Cisco Email Security can block malicious emails sent by threat actors as part of their campaign to gain network access. This is just one example of how Cisco Threat Response can protect email as a threat vector.
All you have to do is peek into your personal email spam folder to find bad actors trying to gain access to you and your network through malicious, compromised, or spoofing emails. In fact, 85% of all email in April 2019 was spam, according to TalosIntelligence. Your network must be prepared for the inevitability of a threat delivered via email.
How Does Cisco Email Security Integration Work?
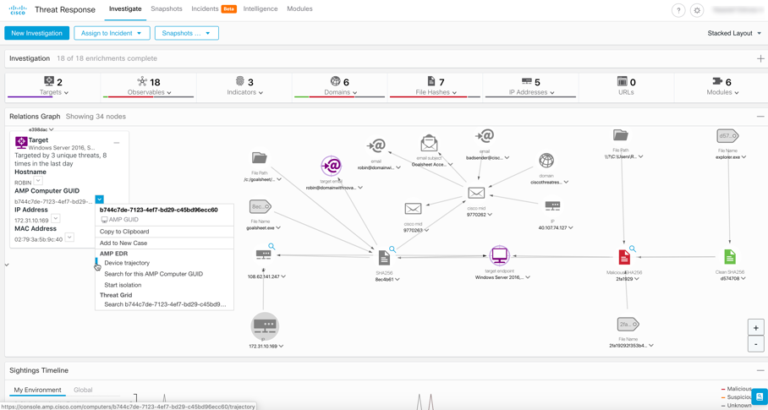
Without a single console to monitor network threats, email has been a difficult vector to protect. However, security architecture integration enables a SOC analyst to identify users who receive a malicious file, quarantine the file, and block the domain the file is reaching out to, without switching interfaces. Faster incident response times are possible because Threat Response provides the user a full picture of the attack, and immediate access to a broad array of integrated protective and mitigative technologies.
Cisco Email Security enables deeper visibility in Cisco Threat Response at multiple layers in an attack’s trajectory, including DNS, endpoint, and now email. With each integration, Threat Response provides enrichment of known attack data, and users can pivot directly into other Cisco Security product consoles to quickly access deeper details of the threat. Users are able to take action immediately through the Threat Response console by blocking the threat vector and associated malicious infrastructure.
Cisco Email Security provides information and context via the Cisco Threat Response platform on email-based threats, by responding to requests for enrichment of elements such as email subject, file name or sender email address, to name a few. Here’s how this works. Your Security Management Appliance (SMA) registers to Cisco’s cloud Security Service Exchange (SSE) and initiates a connection for SSE’s API proxy. Threat Response communicates with the SMA via this SSE proxy, which relays requests for enrichment to your email security solutions (whether on on-premise or in the cloud) and forwards responses back to Threat Response. Emails are never sent to the Threat Response or SSE clouds, and raw log data is not stored in the cloud. By providing this insight at the email messaging layer, Threat Response allows responders to find email-borne threats before they manifest on the endpoint.
Alternatively, in one of the recent releases, we have enabled direct integration of Email Security Appliance with Cisco Threat Response, without the use of SMA, which allows customers who have made investments in Email Security but do not use an SMA to benefit from Cisco Threat Response as well. In this scenario Cisco’s cloud Security Service Exchange connects to ESA directly, and SSE allows an ESA to register with the Exchange, while Cisco Threat Response is provided with an explicit permission by a customer to access the registered devices.
Check out this video to get an overview of the benefits of using Cisco Threat Response and Cisco Email Security together.
Cisco Threat Response Enables Detection to Remediation in 2 Clicks
It’s clear that integrated architecture improves security, drives cost efficiencies, and boosts productivity. And according to Forrester, our customers have seen as high as 70% improvement in security operational efficiency by implementing an integrated architecture.
Cisco Threat Response enables your Cisco Security products to integrate seamlessly and begin working to detect, investigate, and remediate threats. The information that you need across your deployed Cisco products is available immediately in one interface. This allows you to more quickly and intuitively formulate your response plan, while also helping you enact the plan with common response actions available directly and immediately in the Cisco Threat Response interface.

Cisco Security solutions continue to be integrated and add more value to the platform. In addition to Cisco Email Security, Threat Response opens visibility into a variety of contexts:
- Users have visibility into the endpoint with Cisco AMP for Endpoints.
- Visibility into content and edge security can be obtained with the above integration by configuring those devices into the AMP for Endpoints UI via the Unity feature.
- Cisco Umbrella provides a portal into domain resolution requests and associated network activity.
- Cisco Threat Grid provides access to context-rich automated malware analysis and threat intelligence.
- Open API integrations support additional solutions already present in a customers’ security setup.
- Threat intelligence from Cisco Talos and third-party sources integrates automatically to research indicators of compromise (IOCs) and quickly confirm threats.
By providing automated integration across several Cisco Security products, including Email Security, Threat Response provides a seamless experience that serves as a foundation for fast, efficient incident investigation and response.
Building Value Through Integration
As previously mentioned, the value of Threat Response is in the integration of security architecture to enable the SOC to have all needed information and an increased level of detail to make a determination and take action against a network threat. These integrations continue to streamline processes and create cost efficiencies for our customers.
With Cisco Email Security, keeping email secure is no longer a time-intensive task. With its integration into Cisco Threat Response, email threats can now be solved in just minutes. While this is the first integration that steps into the middle ground between the external network and the endpoint, stay tuned for continued integrations that add further visibility into content as it traverses across the network.
Check out the Cisco Cybersecurity Report that examines email security from three angles: the current state of the challenges of security practitioners, the mechanisms behind phishing attacks, and recommendations for defenders. Cisco Threat Response adds enhanced protection to your network against email threats like malware, phishing, spoofing, ransomware, and business email compromise
If you’re interested in giving Cisco Threat Response and Cisco Email Security a test drive, be sure to visit our webpage or create an account in the U.S.or EMEAR to get started today.
Want to keep up to date on Cisco Threat Response? Now you can! Subscribe here to receive alerts every time a new blog is posted.
The post Combat Modern Day Plague in Security with Email Security and Cisco Threat Response Integration appeared first on Cisco Blogs.

