
Reflecting on Black History Month at Autodesk
February 28, 2022
Glocomp & NSFOCUS Food & Wine Pairing Dinner 2021
March 1, 2022Cyber Asset Attack Surface Management with Cisco Secure Cloud Insights: Beyond CSPM
In today’s digital-first world having enterprise grade information, services, and workloads in the cloud is becoming increasingly important for success. Nonetheless the lack of asset visibility that haunted private networks has not disappeared in the cloud era; it has been transferred, or some may say even aggravated.
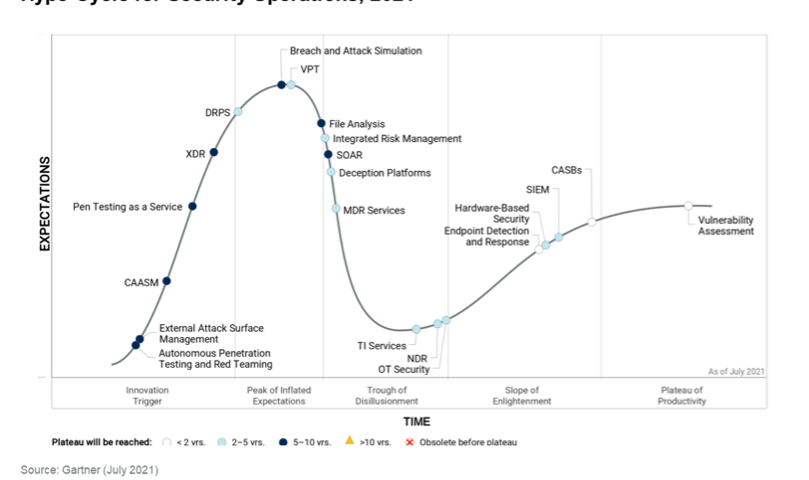
In its Hype Cycle for Security Operations, Gartner has defined Cyber Assets Attack Surface Management (CAASM) as “an emerging technology focused on enabling security teams to solve persistent asset visibility and vulnerability challenges”. This tackles our lack of visibility concerns. However, it extended CAASM’s definition to include “enables organizations to see all assets (both internal and external) through API integrations with existing tools, query against the consolidated data, identify the scope of vulnerabilities and gaps in security controls, and remediate issues.” This highlights the fact that while there is no lack of data, processing and assessing remains challenging due to silos. This is where Secure Cloud Insights (SCI) steps in.
Secure Cloud Insights (SCI) is a technology that delivers multiple CAASM’s benefits:
- Ease of provisioning: Native API integrations make provisioning and deploying SCI a simple task. A wide range of integration types are supported such as cloud providers, vulnerability assessment tools, code repositories, identity sources, endpoint solutions, workflow
- Cyber asset visibility and classifications: Numerous pre-defined integrations feeds SCI with diverse assets and asset types and their associated “state” or “configuration” that defer from one integration to the other. The graph database and the classification engine play a big role in grouping assets by their class and type. For example a data store class contains asset types such as an S3 bucket, EFS, google storage bucket, etc.
Mapping asset relationships: SCI maps asset based on their relationships as shown below: A security group ‘Allows’ access to the internet and ‘Protects’ an EC2 instance (Figure 1).

This Instance ‘Uses’ a specific role (Figure 2)

This role is ‘Assigned’ a policy that ‘Allows’ full control to an S3 bucket(Figure 3)

This graph not only reveals the connected asset types with various relationships but also expands to disclosing the risk of having the publicly accessible instance compromised, which leads to the exposure of data in the private S3 bucket to leakage or destruction.
- Flexible asset querying: SCI’s simple query language and relationship graph database structure make it easy to query the data to answer questions that are the bread-and-butter of security teams, such as:
- Which hosts are vulnerable in my environment?
- Who has not completed the required security training?
- Are my data stores encrypted at rest?
- …
- Expansive Question Library: The querying language is expanded in SCI with a built-in library of more than 650 security questions that makes it easier to answer challenging enquiries with simple spoken language without having to learn the technicalities of the underlining querying language.
- Compliance reporting and configuration drifts detections: SCI supports pre-built security compliance frameworks including SOC2, HIPAA, FedRAMP, CIS benchmarks etc. SCI simplifies configuration drift detection with always-on compliance and gap analysis that does not wait for auditors to knock asking for reports. Moreover, SCI eliminates another layer of time-consuming processes by removing the need to contact system owners for evidence collection by automating it where applicable.
Secure Cloud Insights ticks all the boxes for a CAASM solution and goes beyond by offering simplicity and flexibility in operation with built-in customizable question library and reporting features that focus on security gaps and compliance drifts.
In fact, every feature is built on top of graph relationship database and the simple querying language that makes any piece of data accessible and visible with a simple modification of the query as per the user needs. SCI emerges from the realm of CAASM and CSPM by turning into a framework that answers security team challenges around visibility, compliance, threat risk, incident impact investigation, threat blast-radius and many others with simple few clicks.
We’d love to hear what you think. Ask a Question, Comment Below, and Stay Connected with Cisco Secure on social!
Cisco Secure Social Channels



