
Bagaimana teknologi awan mampu mengukuhkan ekonomi digital Malaysia
July 19, 2021The Security Startup Ecosystem and the Trends Cisco is Watching
July 21, 2021Enabling Zero Trust on the Endpoint
Things are changing in the world of endpoint security. Part of this change has to do with how organizations are digitally transforming themselves to accommodate the abrupt shift to remote work in 2020. In March of that year, for instance, Gartner revealed that 88% of business organizations around the world had encouraged their employees to work from home due to the pandemic.
The shift to remote work led employees to connect to the corporate network using a variety of new personal and corporate-owned devices. This expanded attack surface made endpoint security more difficult for organizations, as it increased the number of devices that security teams need to identify, protect and monitor. That’s more work for personnel who are already struggling to keep up with a constantly evolving digital threat landscape.
The Need for Zero Trust and How Endpoint Security Can Help
Endpoint security should not be an island unto itself. It needs to be an integral part of an organization’s broader digital security strategy.
That explains why we’re seeing so much interest around adopting Zero Trust. Indeed, a recent survey found that more than a third (39%) of respondents were in the process of fully embracing Zero Trust. An additional 39% of survey participants said that they were moving towards integrating a zero-trust model into their own workplaces.
These findings aren’t surprising; Zero Trust mirrors the evolution of organizations’ IT environments. As employees, customers, and partners engage with cloud-delivered applications and data from diverse, potentially insecure environments, for instance, the use of zero-trust models is becoming more common in security architecture. Zero-trust requires fine-grained access controls to applications and data. What’s more, a Zero Trust approach that includes endpoint security as a key control point not only provides a more robust protection, it also helps reduce the risk of compliance violations by unifying user and endpoint security to verify trust at both the user and device levels before allowing access to sensitive applications and data.
Realizing the New Reality of Endpoint Security
One of the highest priorities for a security team is to prevent unauthorized access to resources that could result in data leakage or lateral movement across their environment. However, determining appropriate access to business resources and implementing role-based access control is often challenging.
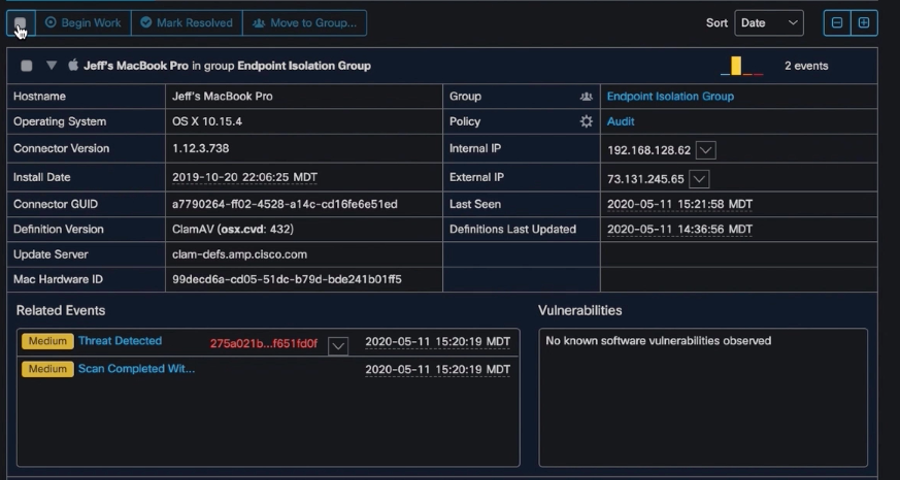
It doesn’t need to be. With the Trusted Endpoint approach by Cisco Secure Access by Duo (formerly Duo) and Cisco Secure Endpoint (formerly AMP for Endpoints), you can restrict users who are not in compliance with your security policy automatically. Cisco Secure Endpoint provides visibility to devices that are compromised and prevents users who are using these compromised endpoints from accessing business critical applications, enabling a strong Zero Trust defense.
Here, we can see that Cisco Secure Endpoint has detected signs of compromise on a particular user’s laptop. By integrating with Duo, we have removed any chance that the user is able to access protected applications before a security analyst gets to triage the event.

When we pivot over to Duo, we can observe that the user tried to access an application and was prevented from doing so. These attempts are logged with an explanation of why the user was blocked. After the compromise is taken care of, the user can be unblocked.

In this demo, one of our Technical Marketing Engineers shows the configuration in real time.
EMBED VIDEO https://www.youtube.com/watch?v=r2I6GymMYS8&list=PLFT-9JpKjRTCLWTqbTv85ECdyehWGFQ_d&index=12&ab_channel=Cisco
For more information on setting this up, please visit the following:
The Importance of an Integrated Approach
Zero Trust (ZT) has gained significant momentum in the past 12 months. This has been heavily driven by the global shift to remote work, not to mention new developments in the digital threat landscape. As organizations strive to provide least-privileged access to applications and data, endpoint security solutions can play a critical role in enabling Zero Trust.
Because most endpoint security solutions operate in isolation, organizations are limited to the visibility that they can obtain from a single, local system. This lays the groundwork for more sophisticated attacks to evade endpoint controls by mimicking local user behavior. By contrast, when endpoint security works collectively with identity and access, email security, data protection, and other controls that are a part of an organization’s broader digital security strategy, the combination can more easily identify account takeover (ATO) fraud attempts along with other impersonation attack techniques.
This integrated approach to security controls provides the necessary context to support zero-trust models on an ongoing basis.
Sign up for a free Cisco Secure Endpoint trial

