
The Next Revolution of WiFi and Why it Matters
March 6, 2020
Starting Your Microsegmentation journey
March 7, 2020Enforce Endpoint Compliance and Cyber Hygiene With Duo Device Trust
Cisco’s recently released their 2020 CISO Benchmark Report that makes several key recommendations for security professionals to achieve a zero trust vision. The following are a couple of recommendations that are relevant to the discussion in this blog regarding device trust:
- More than half (52%) of the respondents said that mobile devices are now very or extremely challenging to defend. Solution: Have an up-to-date asset inventory that distinguishes between managed and unmanaged devices, providing a hygienic check on them as part of an integrated IT and security function.
- Forty-six percent of organizations (up from 30% in last year’s report) had a security incident caused by an unpatched vulnerability. Solution: Organizations should maintain an up-to-date inventory of all devices in their environment and perform a risk analysis for any missing patches
Enterprise IT networks have changed significantly in the last few years. Businesses are leveraging cloud and mobile technologies to enable faster digital transformation. At the same time, IT teams need to optimize for cost and productivity.
From a cybersecurity standpoint, this means enabling secure and direct access to business applications for a diverse set of users – remote workers, vendors and contractors; and their devices that typically reside outside of the control of corporate EMM (enterprise mobility management) and MDM (mobile device management) solutions.
Enforcing security policy compliance seamlessly across managed, BYOD and 3rd-party devices poses a significant challenge for the security team. In most cases, IT security teams lack the insights and an enforcement mechanism when making an access decision on endpoints, particularly among the unmanaged devices. There’s a few key checks that organizations should perform before granting access in order to attest whether a device is trustworthy:
- Is the device managed?
- Is the operating system (OS) version and the patch level up to date?
- Is the enterprise antivirus (AV) agent installed and running?
- Is disk encryption turned ON?
- Does the device have a password set?
How Duo Verifies Device Trust
Duo enables organizations to verify the trustworthiness of any device – managed or unmanaged – by providing the following three key capabilities:
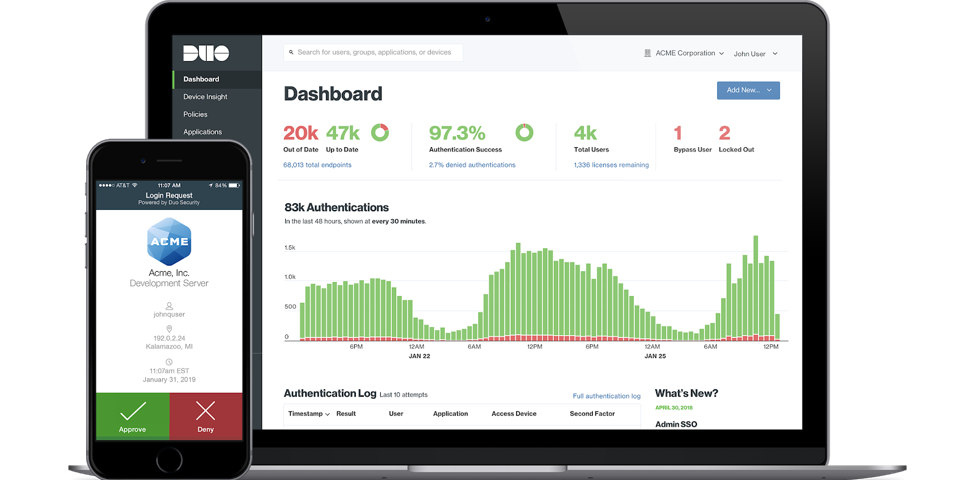
- Complete Visibility: Visibility is important to verify and enforce device trust policies. Duo provides in-depth device visibility across all major operating systems, and helps administrators differentiate between corporate-managed devices and BYOD, based on the enrollment status in device management systems.

Duo’s extensive logging and reporting enables organizations to maintain inventory of all devices accessing corporate resources. A comprehensive dashboard helps administrators understand the overall organizational security posture, and a quick drill-down with a few clicks allows them to identify users that are using risky devices running out-of-date operating systems (OS), browsers, Flash and Java versions. And all of this data can be easily exported to popular log management and analysis tools.
- Assess Device Posture: Duo makes it easy for organizations to gain just the right level of visibility needed to verify the trust of any device that requires access to corporate data. Administrators can enforce corporate security policy compliance and block non-compliant devices at the time of authentication. Duo becomes a critical enforcement point to ensure that users maintain an acceptable level of device hygiene, whether it is updating the OS patch level or enabling security features such as enterprise AV agents and disk encryption, before granting application access.

Duo’s novel approach to assessing device health posture is geared to address the diverse population of managed and unmanaged devices that access enterprise networks. Duo helps administrators ensure that their endpoint fleet is in compliance with corporate security policies and empowers end users with self-remediation, which reduces the number of IT tickets raised or calls to a support help desk.
- Continuous Inspection: Organizations have limited IT resources (staff and tools), and find it tough to effectively respond to endpoint security events, especially when those devices are outside the network. By integrating Cisco AMP for endpoints with Duo, organizations can set a policy to automatically block malware-infected devices from accessing applications. Duo blocks only the device and the user can log in from any other device that is policy-compliant in order to be productive.
Learn more about Duo’s Device Trust.
Use Cases For Duo Device Trust
| Use Case | Duo Feature | Implementation Option |
| Maintain inventory of all devices accessing protected applications | Device Insight | Agentless / Browser-based |
| Enforce risk-based access controls for managed and unmanaged devices (BYOD) | Device Insight
|
Agentless / Browser-based
|
| Device Health App
(MacOS, Windows); (iOS, Android) |
Application-based (offers granular control) | |
| Protect your environment and limit access to corporate-managed devices | Trusted Endpoints
(Works with JAMF Pro, AirWatch/ Workspace ONE, MobileIron, Microsoft Intune, etc….)
|
Certificate-based |
Three Reasons To Choose Duo
- Duo offers the most comprehensive user trust and device trust capabilities in the market today that cater to a wide variety of use cases and a diverse population of workforce devices (managed and unmanaged).
- Duo helps organizations to improve security in a manner that is user friendly and enables productivity. Users are empowered with self-remediation for out-of-policy devices, so security does not interrupt daily tasks.
- Duo is focused on integrating across the Cisco Security portfolio so that customers can reduce their total cost of ownership (TCO) by consolidating security vendors, streamlining security operations and enabling automation.
For organizations, all this translates to reducing cyber risk and enforcing cyber hygiene. Try it for free by signing up for a 30-day trial.
The post Enforce Endpoint Compliance and Cyber Hygiene With Duo Device Trust appeared first on Cisco Blogs .

