
Is Your Guest Network Exposing You to Hackers?
December 17, 2019
Misinformation and Mistakes Continue to Hinder Productivity of UK Construction Firms, Autodesk Research Shows
December 17, 2019Hackers hit Norsk Hydro with ransomware. The company responded with transparency

The bedside phone rang at 4 a.m. in Oslo, Norway. The pre-dawn call filled Torstein Gimnes Are with a drowsy sense of dread. That only deepened when he heard the first words from the other end.
“We may be under attack,” said his IT colleague at Norsk Hydro, one of the world’s largest aluminum companies. Production lines had stopped at some of its 170 plants. Other facilities were switching from computer to manual operations.
Bad news.
It would get worse.

The breach last March would ultimately affect all 35,000 Norsk Hydro employees across 40 countries, locking the files on thousands of servers and PCs. The financial impact would eventually approach $71 million.
All of that damage had been set in motion three months earlier when one employee unknowingly opened an infected email from a trusted customer. That allowed hackers to invade the IT infrastructure and covertly plant their virus.
After hanging up, Gimnes Are, corporate information security officer at Norsk Hydro, immediately phoned the company’s emergency preparedness chief to organize an urgent meeting later that morning.
“This was a company crisis,” recalls Gimnes Are. “IT had already shut down the network and servers to avoid any further spreading. But we didn’t fully know what this was.”
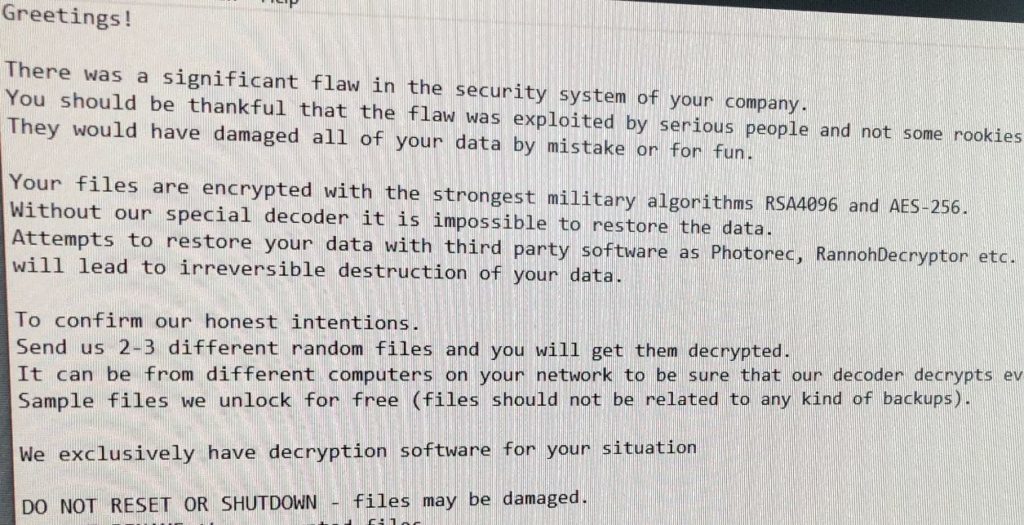
Soon, they all knew its name: LockerGoga, a form of ransomware. It encrypted the files on desktops, laptops and servers throughout the company. It also posted a ransom note on the screens of the corrupted computers.
“Greetings!” the note began. “Your files are encrypted with the strongest military algorithms. … We exclusively have decryption software for your situation … .”
The note demanded the company pay a ransom in bitcoins and added, “The final price depends on how fast you contact us.”
At the emergency meeting, Norsk Hydro executives made three swift decisions: They would pay no ransom, they would summon Microsoft’s cybersecurity team to help restore operations and they would be fully open about the breach.
That third choice gained accolades from security experts around the world because it bucked the usually secretive responses many organizations employ after getting hacked.
Senior staff hosted daily webcasts and answered audience questions. Executives held daily press conferences at their Oslo headquarters, posted updates to Facebook, welcomed journalists into their operations control rooms – and even launched a new company website during the attack’s first week.
Transparency is core to the Norsk Hydro culture, says Halvor Molland, senior vice president of media relations. By issuing frequent, candid communications about the events, the company also sought to expose the shadowy tactics of cyber criminals and maybe curb similar threats.
“We wanted to help other industries learn from our experience,” Molland says. “This way, they can be better prepared for situations like this and not have to go through what we did.”
In the first hours of the breach, Norsk Hydro requested assistance from Microsoft’s Detection and Response Team (DART), which goes onsite to support companies under attack and provides remote, proactive investigations.
The case was designated “maximum severity,” says Jim Moeller, a DART member and a specialist in cyberattack response. He was dispatched to a small city near Budapest, Hungary, home to one of Norsk Hydro’s largest aluminum manufacturing plants. Production there was offline.

Moeller spent three weeks in Hungary, building a team from regional engineers and architects. The team’s initial task was to help the company recover and reconstitute its business operations and services, Moeller says. Other DART members flew to Oslo.
“With our guidance, Norsk Hydro was able to mitigate the mechanism by which the attacker was able to launch the attack,” Moeller says.
They got to know LockerGoga, which also attacked Altran Technologies, an engineering consultancy company in France, and two U.S. industrial firms – Hexion, based in Ohio, and Momentive, based in New York.
In Oslo, a team of internal and external forensic investigators determined that in December 2018, the hackers had weaponized one email attachment sent by a trusted customer employee to an employee at Norsk Hydro – part of a legitimate conversation, Gimnes Are says.
“They equipped it with a payload to install a Trojan software on the PC of the Hydro employee,” Gimnes Are says. “This Trojan software was discovered by our antivirus a few days later. But that was already too late. By then, the attacker had built an initial foothold in our system.”
At first, the ransomware compromised standard users within the Norsk Hydro computer network. Then it captured administrative credentials, allowing the hackers to command the entire IT infrastructure, Moeller says.
“Once the attacker controlled the environment, they chose to deploy ransomware via a manual push from (Norsk Hydro’s) own domain controllers,” Moeller says.
“This was another example of recent attack behavior where the attack group uses Advanced Persistent Threat (APT) entry strategies to deploy more commodity-level malware in the hopes of faster monetization with lower attack investment,” Moeller adds.
But Norsk Hydro was not about to pay a single bitcoin to the hackers or negotiate to recover the locked files. Instead, they opted to restore their data through trusted back-up servers.
“What would you get from paying a ransom in such an attack?” Gimnes Are asks. “You will potentially get back your encrypted data – if the attacker gives you the key. Paying the ransom would not help you to rebuild the company infrastructure, all the servers, all the PCs, all the networks.
“Paying the ransom will not help you out of the situation. You will need to rebuild your infrastructure to be safe and be sure that the attacker is not still part of it,” he adds.
At Microsoft, Eric Doerr serves as general manager of the Microsoft Security Response Center, which protects customers from being harmed by security vulnerabilities in Microsoft’s products and services. The center also rapidly repulses attacks against the Microsoft Cloud. Doerr strongly promotes transparency among organizations that suffer cyberattacks.
“Norsk Hydro set the example for the industry in this incident,” Doerr says.
“Choosing not to pay the ransom and digging in with DART to evict the attacker is great. Sharing those learnings with the world is priceless. When companies do this, it makes us all better and makes the attackers work harder,” he adds.
Of course, some companies facing a ransomware attack may be highly tempted to pay bad actors to regain their hijacked data. But paying hackers doesn’t guarantee that a company will ever recover the goods, says Ann Johnson, Microsoft’s corporate vice president of cybersecurity solutions.
There’s a smarter way – following the plan executed by Norsk Hydro, says Johnson, whose team oversees DART.
“Your data is a strategic asset for you, and for cybercriminals. That’s why they want it. It is also why your data must be protected, and it should be backed up,” Johnson says.
At the same time, companies must invest in cybersecurity, she adds.
At Norsk Hydro, for example, the IT department works to increase security awareness among its employees, says Molland, the media relations SVP. That includes sending workers test emails to help train them to look for common phishing tactics like fake login pages and malicious attachments.
If companies fail to commit to cybersecurity, Johnson warns, bad actors will become repeat customers.
“You’ve likely seen signs that read, ‘Don’t feed the birds,’ when dining at an outdoor café. That’s because the birds will keep returning to the same places where they know it’s easy to be fed. It’s the same concept for cybercriminals,” Johnson says. “They know if you have weak cyber-defenses, and they will want to exploit those weaknesses over-and-over.
“The best defense is to ensure you have the right combination of people, processes and technology. We recommend you implement multifactor authentication, have a mature update process, and back up your data,” she adds.

In Hungary and Norway last March, DART members helped Norsk Hydro develop safe processes to restore their servers with an improved security posture. They also educated the company about the current threat landscape and known attacker behaviors to help reduce the risk of future attacks, Moeller says.
Inside Norsk Hydro, the internal response focused on multiple fronts. They launched old-school methods to resume full production and repair business operations. And they worked to protect the safety of employees and the environment.
“We operate heavy machinery. If the power is lost in an uncontrolled manner, it could risk severe safety incidents for people,” says Molland, the media relations SVP.
“Safety is always first priority with us. Secondly, it’s the concern for the environment and ensuring we don’t have any uncontrolled emissions (due to sudden machine stoppages) out to the air, land or water.”
Executives handwrote signs warning of the cyberattack, photographed them with their smart phones and texted the images to managers at Norsk Hydro plants and offices around the world. At those facilities, the staff used local printing shops to create paper signs, posting them on entryways, stairwells and elevators for employees to read as they arrived for the workday.
“Please do not connect any devices to the Hydro network. Do not turn on any devices connected to the Hydro network. Please disconnect devices from the Hydro network,” read some written alerts that also carried a simple signature: “Security.”

The entire workforce did their jobs with pen and paper during the attack’s first days. Some plants switched to manual procedures to meet manufacturing orders. Retired employees – familiar with the old paper system – volunteered to return to their plants to keep production rolling.
“The way we pulled together to make the company come through the situation in one piece and get back into production has been an extreme team-building session,” Molland says.
“We have an organized emergency preparedness methodology within the company – in the corporate level, in the business area and at the plant level,” he adds. “That worked to our benefit. When this hit us, we were able to handle the situation in a constructive, organized manner.”
In other words, prevention is important but locking out all cyberattackers should not be a company’s sole security focus, says Jo De Vliegher, Norsk Hydro’s chief information officer.
“If hackers want to get in, they will get in,” De Vliegher says. “We now have an improved incident response to make sure that – should something similar happen – we are much better equipped to limit the damage in time and geography.”
Norsk Hydro reported the incident to Norway’s National Criminal Investigation Service (Kripos). The case remains under investigation, Molland says.
Video and photos courtesy of Norsk Hydro.
The post Hackers hit Norsk Hydro with ransomware. The company responded with transparency appeared first on Microsoft Malaysia News Center.

