
Microsoft strengthens leadership team in Malaysia with three new appointments to deliver digital success to customers
February 16, 2022
Relevant and Extended Detection with SecureX, Part Four: Secure Cloud Analytics Detections
February 18, 2022Headcount alone isn’t enough for your headaches
We’ve all heard the phrases: An ounce of prevention is worth a pound of cure; failing to plan is planning to fail. But sometimes even the best plans fall short when attackers come calling on your enterprise.
Helmuth von Moltke was famously quoted as saying, “No plan of operations extends with certainty beyond the first encounter with the enemy’s main strength.”
A modern translation would be, “No plan survives contact with the enemy.”
This is sage advice. There is an overwhelming need to ensure enterprises can respond to threats in a timely manner. And in part three of our five-part blog series on the newly published Security Outcomes Study, Vol. 2, we’ll look at the importance of speed in threat response.
To support the enterprise’s ability to react to incidents, you need three key elements:
- Strong security staffing
- Defined repeatable processes
- A better hammer
Everything starts with a strong security staff
If you build a house, it must have a solid foundation. When you are building your security practice, that same logic holds true. However, with a security practice, your foundation is your staff. When you have a good staff that you can depend on, you can respond to security incidents in a timely manner.
Let’s be honest with ourselves. If we’re unable to respond to security incidents in an expeditious fashion, then the attackers will start operating from high ground. And, unfortunately, it is entirely possible that, as a defender, we will not be able to regain that position, putting us at a significant disadvantage.
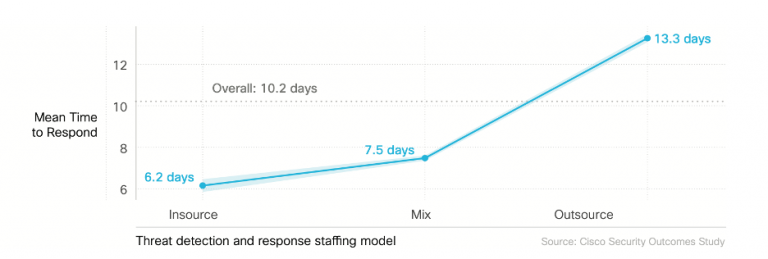
So, what kind of team makes us less likely to cede the high ground? Internal or outsourced?
The Security Outcomes Study, Vol. 2, found that outsourced detection and response teams were seen as being superior, while the actual numbers told a different story. Internal teams demonstrated a faster mean-time-to-respond of 6 days versus the13 days of an outsourced approach.

Above all else, one statement can be said with full confidence — having a strong, skilled cybersecurity team is of upmost importance. The Security Outcomes Study, Vol. 2 says it best:
[O]rganizations with huge security teams are significantly more likely to achieve strong detection and response capabilities than those with skeleton crews. But head-count alone won’t make all your SecOps headaches go away or guarantee success. Furthermore, even the differences between the smallest and largest staffing ratio don’t account for the performance boost associated with having strong people resources… Thus, we’re left to infer that quality is equally—perhaps even more—important than quantity when it comes to building strong threat detection and response teams.

Nearly 92% of all the organizations polled in the study with strong people, process, and technology achieve advanced threat detection and response capabilities. That’s a 3.5X performance increase compared to SecOps programs unable to deliver on these three pillars.
Focus on developing solid repeatable processes
Defined repeatable processes are key tools for teams to reduce risk in their enterprises. We’ve all experienced the “joy” of running around with our hair on fire at a previous employer (or current one if you’re unlucky) when something goes horribly awry. A clear process can help a great deal in tackling an incident and making sure nothing gets missed. A clear process can also help you ensure that the right tools are used, the correct people are engaged, and the necessary stakeholders are informed in a timely manner.
To improve security, one must have a solid strategy in place, such as a Zero Trust strategy. This can reduce overall risk by mitigating the dreaded “whoops factor” as much as possible. Our report also noted that organizations claiming to have mature implementations of Zero Trust or Secure Access Service Edge (SASE) are about 35% more likely to report having a strong SecOps than those with developing programs. These results illustrate the many benefits modern architectures can bring to cybersecurity programs.
And while we’ve touched on staffing and processes, we should also talk about technology when dealing with the speed of a timely incident response.
As with any incident, we must be cognizant of the fact that there are many pieces in motion. Subsequently, there may be multiple vendors that need to issue patches or bug fixes to address a vulnerability that arises. Once the patch is received by the customer, they need to do regression testing in their own lab environment to make sure nothing is accidentally broken once it is moved into production.
Get a bigger hammer to smash those threats
To protect the enterprise from potential malfeasance on the part of criminals, organizations must rely on the right tools to get the job done.
The idea here is simple on its face but is difficult to execute. Having a dependable team, defined processes, and the right tech to address security issues as they arise works well—if no shortcuts are taken.
Ultimately, having a security team onsite will cut response times in half as mentioned above. Meanwhile, processes will help reduce the “whoops factor” and deliver the right tools to build out the Zero Trust and SASE architecture, further reducing the chances of something going wrong.
So, build it once…and build it right!
Just one piece of the puzzle
While timely incident response is important, it’s just one piece (albeit, a large piece) of building a world-class security practice. Our research suggests that there are five critical pieces to any successful security organization: a proactive tech refresh strategy, well-integrated technology, accurate threat detection, prompt disaster recovery, and, of course, timely incident response.
While timely incident response is critical, a strong, confident team – even a small one – can deliver the same effective results as a larger one with more abundant resources. And once you’ve developed that library of repeatable processes, you’ll enjoy less overall risk, much better results, and world-class cybersecurity. To deep dive on each of these, read the Security Outcomes Study, Vol. 2 today or get highlights from each of the other four critical cybersecurity practices from my colleagues in our ongoing blog series.
We’d love to hear what you think. Ask a Question, Comment Below, and Stay Connected with Cisco Secure on social!
Cisco Secure Social Channels
Instagram
Facebook
Twitter
LinkedIn

