Snort 3: Rearchitected for Simplicity and Performance
June 2, 2021
Autodesk Construction Cloud Global Focus Expands with Workflows that Support ISO 19650
June 2, 2021Introducing continuous remote worker visibility and expanded data collection with Secure Network Analytics Release 7.3.2
We are very excited to announce new Secure Network Analytics features! With release 7.3.2, we have furthered our efforts to extend the zero-trust workplace to anywhere on any device through significant enhancements to Secure Network Analytics’ ability to provide complete and continuous remote worker visibility and have also expanded data collection from integrated Cisco Secure solutions to offer extended visibility beyond the parameters of the traditional network, and more!
Preamble: The great network visibility blackout of 2020
It’s no secret that last year’s abrupt exodus away from corporate offices presented organizations with novel challenges related to monitoring and securing their newly remote workforce. To briefly level-set, let’s take a quick step back in time – way back to 2019 before the “work from home (WFH) era” had begun to illustrate the gravity of the paradigm shift that occurred over the past two years and its security implications. Organizations had always historically experienced visibility gaps into employee activities whenever their users were off-VPN while working remotely. However, back then, although these occasional gaps in visibility did naturally result in minor and temporary increased organizational risks, the overall volume of non-VPN-connected remote work that took place was so low and infrequent that it was considered to be negligible and ignored.
Then, fast-forward to March 2020, where practically every organization was hit with a prolonged and complete employee activity visibility blackout. This “visibility blackout” led to an explosion in need for remote access from anywhere and on anything, effectively exponentially expanding threat surfaces and increasing opportunities for attackers. To summarize, visibility evaporated, and meanwhile, organizational risk levels spiked parabolically.
SecOps teams were left in the dark and found themselves asking questions like, have any of our users visited malicious URLs? Has anyone “gone rogue”? Are employees exfiltrating sensitive proprietary data? Have users’ devices been unintentionally compromised and are now demonstrating command and control (C&C) activity? Are we facing compliance-related and broader organizational risks due to employees running outdated and vulnerable operating systems that need patching?
Complete. Blackout.
Complete and continuous remote worker visibility
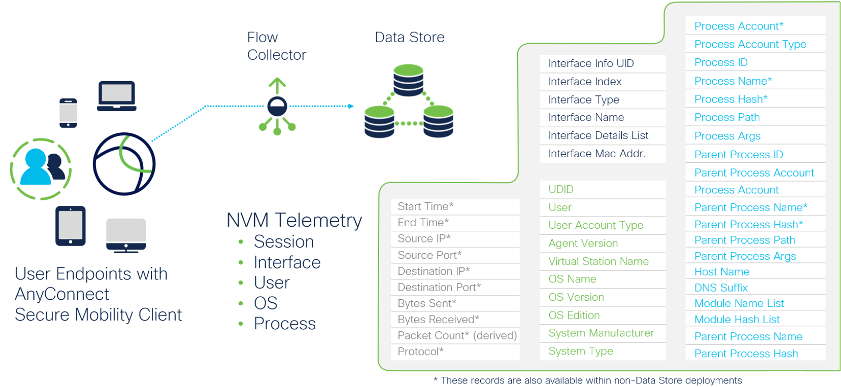
Cisco Secure Network Analytics began to address this whole “WFH visibility blackout conundrum” with Release 7.3.1 by introducing endpoint Network Visibility Module (NVM) data as a primary telemetry source to provide organizations with continuity in remote worker monitoring and visibility without requiring NetFlow telemetry to be present. This greatly simplified deployments and enabled customers to obtain more visibility.Starting today, with Release 7.3.2, we’re further extending this capability with the Data Store now supporting all NVM telemetry record collection to offer 100%-complete and continuous remote worker visibility. So now, whenever a user works either on-network or remotely – be it at home or a local coffee shop – and thus off-network, without tunneling through a VPN, are optimizing their remote work experience with split tunneling, all their activity will be stored locally. When workers eventually turn their AnyConnect VPNs back on, the Network Visibility Module will phone home and send logs of all their user activities back to Secure Network Analytics.
Lights back on!
This gives security practitioners the continuity in visibility that they need by allowing them to monitor remote worker telemetry through the collection and storage NVM endpoint records without the need for NetFlow to gain user and device context. Security teams can now gain visibility into activities that they were previously blind to, such as:
Additionally, with Release 7.3.2, customers that are using NVM data along with a Data Store deployment are also gaining the following benefits:
- NVM telemetry records can be collected, stored, and queried in the Data Store
- New NVM reports that are now available in the Report Builder application
- The ability to define customized security events based on NVM data-specific criteria
- All Endpoint Concentrator functions are now fully managed by the Flow Collector

Expanded data collection to provide further extended visibility and enhanced context
Additionally, by leveraging other Cisco Secure offerings, Secure Network Analytics now also offers expanded visibility and enhanced context beyond the parameters of both the traditional on-premises network, as well as public and private cloud network environments. In addition to NVM data, further expanded visibility and additional context can be attained by collecting Cisco Firewall logs from Cisco’s Security Analytics and Logging offering to extend visibility to the network perimeter, as well as through the Cisco Telemetry Broker, which is capable of brokering, filtering, and transforming multiple data formats into IPFIX records and other Secure Network Analytics-compatible data formats.
Introducing Security Logging and Analytics On-premises
Security Analytics and Logging (SAL) is now supported as an on-premises, enterprise-class storage solution for large-scale firewall deployments. SAL provides central log management to streamline IT operations.
The SAL On-premises solution is an improved architecture compatible with all of Cisco’s FTD and ASA firewall devices, and capable of storing all firewall connection and security events on-premises with the Data Store to offer drastically improved log ingest capacity and extended log retention periods. SAL On-premises also supports a fully qualified remote query API that enables the Cisco Secure Firewall Management Console (FMC) to populate its event viewers and dashboards and support its reporting and analysis capabilities. As a result, SAL On-premises offers significantly improved firewall log management scalability by delivering the following benefits:
- Cross launch capability from the FMC with context into the Security and Logging Analytics Dashboard
- Data available to the FMC to support remote queries
- Increased log ingest capacity by a 5x magnitude of 100K events per second (EPS)
- Significantly longer-term log storage periods increased by a 50x magnitude of 30 days at 100K EPS
And to summarize the implications of the above two bullets, with a retention period of 30 days at 100K EPS, SAL On-premises effectively offers a literal 300x – or a whopping 30,000% – increase in firewall log storage capacity!
Lastly, since this new capability was built natively on the Secure Network Analytics platform, it can seamlessly correlate both firewall and network logs and offer expanded visibility and enhanced context that extends from internal on-premises traffic to the network perimeter.

The Cisco Telemetry Broker
The Cisco Telemetry Broker (CTB) further expands Secure Network Analytics’ data collection capabilities by ingesting network telemetry from various sources, transforming the data format into IPFIX records, and then forwarding that telemetry to Secure Network Analytics. For example, CTB can ingest on-premises network telemetry, including NetFlow, Syslog, IPFIX, and cloud-based telemetry sources, such as AWS VPC Flow Logs, and transform them into IPFIX records or other Secure Network Analytics-compatible telemetry sources.

As illustrated in Figure 3, the Cisco Telemetry Broker can enable users to gain complete visibility across their hybrid-cloud environments and monitor them with Secure Network Analytics.
Summary
Today’s network environments are vast and complex – spanning from traditional on-premises offices to hybrid-cloud environments, as well as to remote workers’ home networks. Likewise, today’s organizations need network detection and response solutions (NDR) to attain comprehensive and continuous visibility and threat detections across their expanse network environments. Unfortunately, however, not all NDR tools are created equal. Choosing the right one is critical to ensuring that your organization stays a step ahead in the arms race that is network security.
Only Secure Network Analytics rises to this challenge by offering the most comprehensive and context-rich visibility – that spans across all your network environments and extends even further out, across your broader environment –paired with its world-class and time-tested analytics to deliver the broadest and most high-fidelity behavioral-based detection capabilities.
Don’t settle for anything less. Learn more about Secure Network Analytics or try the solution out for yourself today with a free visibility assessment.
To learn more about this release, check out the Release 7.3.2 Release Notes.

