How to Build an Integrated Security Posture Using XDR
December 6, 2021
Spacemaker one year in: Continuing product innovation and advancing Autodesk’s platform vision
December 7, 2021Presenting the Security Outcomes Study, Volume 2
What if you could build a successful, world-class security program with just five practices?
And what if shifting focus to these areas could put your security program ahead of 79% of other organizations? Our latest cybersecurity research study suggests that this is not only true but is also a tangible reality for organizations that choose to follow some practical steps.
Over the past nine months, we’ve orchestrated in-depth data analysis against our very own prior research—the first annual Security Outcomes Study. Now, we’re excited to bring you those findings in the report’s second edition: Security Outcomes Study,Volume 2: Maximizing the Top Five Security Practices.
5,100+ IT and cybersecurity pros chart the way forward
Cybersecurity teams must always up-level their own technology and strategies but, with limited time and resources, may find themselves asking questions like: Should I request funds for this initiative? Should I dedicate time and energy to this project? There are so many things to do—what’s the most important priority? Where do I start?
These questions are critical to cybersecurity success, but where do IT and security professionals go to answer these questions? Industry peers? News outlets? There is value in gathering opinions from these areas, but the scope is limited. Answering high stakes questions like these requires something else. Something bigger.
Enter the Security Outcomes Study, Volume 2. This vendor-agnostic cybersecurity research report offers a data-driven understanding of how you can achieve success in your own security programs. Plus, get some insight into how cybersecurity professionals are performing across industries.
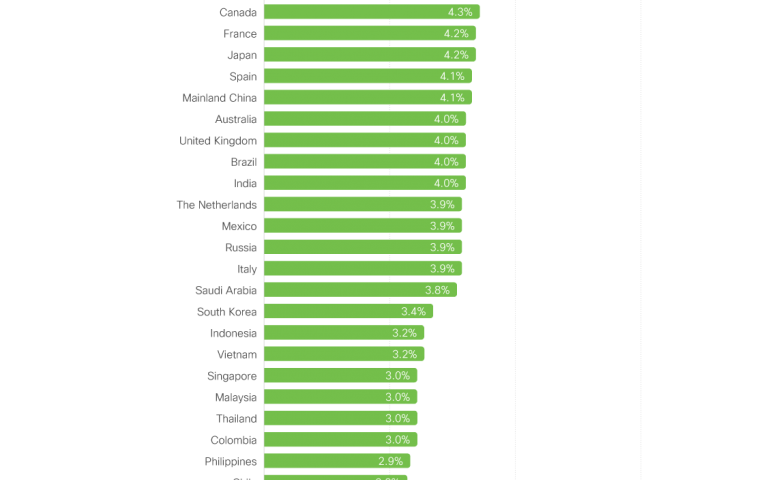
And it’s a big study — the largest we have ever done, in fact. We analyzed survey responses from 5,100+ respondents in 27 countries, across dozens of industries and hundreds of organizations of all sizes. We researched alongside well-respected partners, including the Cyentia Institute, to analyze data from a double-blind survey and create this independent, pragmatic study.

Suffice it to say, the conclusions drawn in this report are well-supported. It should be a trusted friend of any IT and security professional that will answer some of their most critical questions.
What’s new with Volume 2
In the original Security Outcomes Study, we examined 25 general security practices and tested how each practice correlates with the achievement of 12 program-level outcomes. Those surveyed self-reported the areas that they felt they were seeing success in, as well as areas where they struggled.
In the first volume of this study, we found that, across the 25 security practices we asked about, five of them stood out from the rest: proactive tech refresh, well-integrated technology, timely incident response, prompt disaster recovery, and accurate threat detection.
So, what makes these practices critical to the success of security programs? In the Security Outcomes Study, Volume 2, we were able to fully answer this question by putting those five key areas under the microscope. For example, Accurate Threat Detection was one of our top drivers, but what technologies, processes, and staffing models help achieve success in this arena? Does automation and orchestration make a difference? What about insourcing or outsourcing threat management?

Over the next few months, we’ll be publishing a supporting blog series, hearing from several of our advisory CISO team members, providing their commentary and recommendations around each of these five most-effective practices. And as those blogs become available, they’ll be linked below. Here’s what you can expect:
1) Driving a Proactive Tech Refresh Strategy
Across the board, organizations that follow a proactive tech refresh strategy report higher rates of successful security outcomes. With 39% of today’s security tech being considered outdated, refreshes and upgrades are critical to warding off threats.
2) Achieving Well-Integrated Tech
When security technologies work together, organizations report a clear increase in security program success. And it seems like integration is the way of the future, with 77% of organizations opting to buy integrated solutions over building them in-house.
3) Preparing for Timely Incident Response
Strong incident response capabilities are a combination of people, processes, and technology. Security programs that assemble a strong team and automate major threat detection and response processes report the highest levels of security operations success.
4) Developing Accurate Threat Detection
Strong threat detection capabilities can give awareness of potential security events without major blind spots. Organizations reporting highly-integrated functions for identifying assets and risks to those assets boasted much stronger (+36%) detection and response capabilities and more security outcomes.
5) Ensuring Prompt Disaster Recovery
Minimize impact of cybersecurity incidents and keep the business rolling through quality recovery practices. Being proactive is key to achieving and maintaining success. Organizations that make chaos engineering standard practice are twice as likely to achieve high levels of success for this outcome.
Turning Your Cybersecurity Up to 11
Cisco Secure wants to partner with organizations in building the strongest cybersecurity practices on the planet. And our hope is that, through this report, organizations can determine which next steps must be taken to get from point A to point B.
The data doesn’t lie. Through this rigorous cybersecurity research, we can specifically point to how these five data-backed practices can bolster your cybersecurity programs and help you achieve better outcomes.
Start your journey by reading our full Security Outcomes Study, Volume 2 report today.
We’d love to hear what you think. Ask a Question, Comment Below, and Stay Connected with Cisco Secure on social!
Cisco Secure Social Channels

