
Autodesk reveals new logo, look, and feel
September 9, 2021
Unlocking citizen-centric smart cities in Asia
September 10, 2021Simplified Insertion of Cisco Secure Firewall with AWS Route Table Enhancement
Cisco Secure Firewall provides industry-leading firewall capabilities for Amazon Virtual Private Cloud (VPC)and resources deployed inside. Customers use these firewalls to protect north-south and east-west traffic.
Typically, we provide north-south traffic inspection in AWS infrastructure by deploying a load balancer and adding firewalls behind it. Another approach uses Amazon VPC Ingress Routing to steer traffic to Cisco Secure Firewalls.
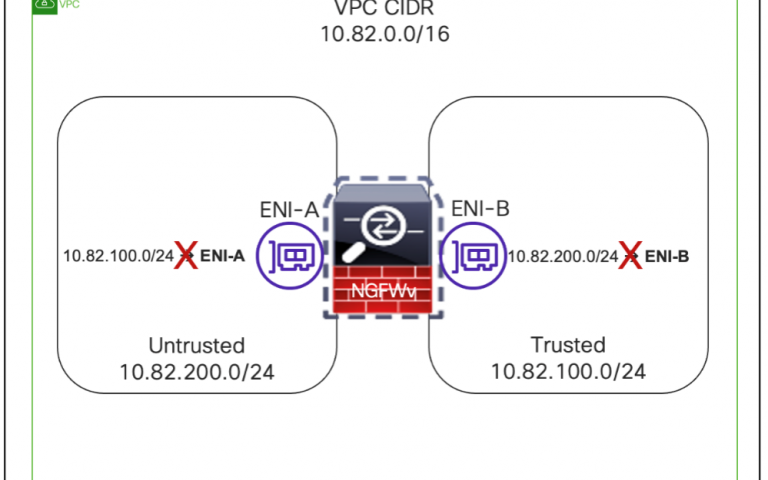
Since the AWS VPC Ingress Routing feature launched, we’ve waited for a similar feature for east-west traffic inspection, as a route in a routing table couldn’t be more specific than the default local route. Figure 1 below illustrates when the VPC range is 10.82.0.0/16, it is impossible to add a more specific route for 10.82.100.0/24 & 10.82.200.0/24.

However, as of today, AWS launched a new feature that enables adding a more specific route in the Amazon Route Table. This feature provides functionality to send and inspect traffic between subnets in a VPC, as shown in Figure 2 below.

The route table in Figure 3 is associated with a trusted subnet and has a route for an untrusted subnet pointing to the trusted interface (Elastic Network Interface – ENI-B) of the Cisco Secure Firewall.

The route table in Figure 4 is associated with an untrusted subnet and it has a route for trusted subnet pointing to the untrusted interface (ENI-A) of the Cisco Secure Firewall.

To see this enhancement, please watch our video on:
Cisco Secure Firewall Easy Insertion with AWS Route Table Enhancement

We’d love to hear what you think. Ask a Question, Comment Below, and Stay Connected with Cisco Secure on social!
Cisco Secure Social Channels
Instagram
Facebook
Twitter
LinkedIn

