
Getting more value from your endpoint security tool #4: Querying Tips for IT Operations
July 9, 2020
The Hunt for the Most Dangerous Cyber Criminals
July 9, 2020SMB Myth Busting: Do smaller organizations face different cyberattacks?
As discussed in last week’s article, there are several myths surrounding the cybersecurity of small and medium sized businesses. One common misconception is that SMBs face different, or fewer, threats than larger organizations. Too often it is assumed that attackers won’t target smaller organizations because there is less pay-off. But is this mentality justified, or does it leave SMBs exposed?
Cisco Product Marketing Manager Hazel Burton sits down with Cisco Advisory CISO Wolf Goerlich and Elevate Security co-founder Masha Sedova to answer this question and debunk some other SMB security myths.
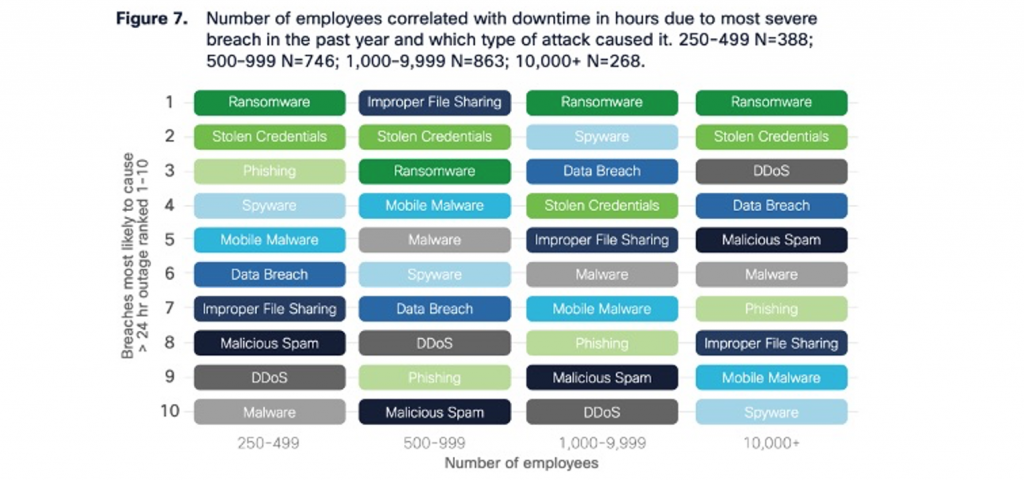
Almost 500 SMBs (defined here as organizations with 250-499 employees) reported the types of attacks they faced within the past twelve months. Their responses were then compared with the number of business hours lost as a result of that particular attack. In the table below, reported attacks are ranked numerically from 1 to 10, with 1 being the most severe.

For example, ransomware is the most likely threat to cause an outage of more than 24 hours for SMBs, while malware is the least likely threat to do so. Looking at larger organizations (10,000+ employees), ransomware is still ranked as the most likely threat to cause significant downtime, but their least severe threat is spyware.
Contrary to popular belief, certain attacks do not discriminate based on size.
Ransomware is ranked as the most severe threat to both SMBs and larger organizations. Stolen credentials are also a significant problem for small and large businesses alike.
The prevalence of ransomware is somewhat unsurprising, but that shouldn’t take anything away from its significance here. It’s much easier for criminals to sell your data back to you than to find another buyer. What’s worse, attackers use their profit to invest in better technologies, making ransomware an even bigger threat.
There are however some threats that affect certain sizes of organizations more. For example, SMBs struggle more with phishing, while larger organizations face significant downtime from DDoS attacks.
Phishing has remained a top-ten security issue for decades.
What can be done to combat such a persistent threat, especially when phishing targets people across your organization?
Masha Sedova advises not to overlook the basics. Investing in technology which blocks known phishing accounts, for example, is a great way to take some of the pressure off non-security employees.
With these solutions in place, organizations can focus on adapting company culture to minimize the impact of phishing campaigns. While most people have good intentions and want to keep their company safe, we all make mistakes. In some cases, reporting that you may be compromised by a phishing attack is met with shaming.
Rather than punishing honest mistakes, leadership should encourage employees to notify security teams. Our Head of Advisory CISOs for Cisco Duo, Wendy Nather, recommends measuring the success of simulated phishing attacks by focusing on the number of employees that report the emails – not by the number of employees that click on a malicious link. When phishing attack reports are celebrated as part of an effective security strategy, employees become security’s strongest link.
It’s also recommended that organizations create a culture where employees understand the context behind why attackers want access to their information, and what their company’s risk factors are. This then truly enables your people to be the company’s first line of defense.
Regardless of size, businesses should prepare for all kinds of attacks.
We’ve all clicked on links that with hindsight, we wouldn’t have. Some of us will also have mistakenly disclosed sensitive information at one point or another, so multifactor authentication is a key consideration for organizations of all sizes, which both Masha and Wolf discuss in this clip.
So, while SMBs and larger organizations are affected differently by certain types of attacks such as phishing and DDoS, they also face many of the same threats. Take a look at the clip for more advice on how to deal with the cyber threats mentioned.
Note: this blog is the second in a five part series. Subsequent blogs to follow.
To read last week’s article on SMB executive leadership and security, please visit SMB Cybersecurity: The real benefits of a top-down approach
To watch the full streamcast, please visit Cisco Chat Live SMB Myth Busting
If you are interested in unpacking more myths surrounding SMB security, consider reading “Big Security in a Small Business World”
The post SMB Myth Busting: Do smaller organizations face different cyberattacks? appeared first on Cisco Blogs.

