
#BreakTheBias: Women in Cybersecurity
March 9, 2022
Introducing the new ‘Defending Against Critical Threats’ report
March 10, 2022Stay on target: How accurate threat detection leads to better defense
The X-Wings began their run across the surface of the Death Star, racing to attack an exposed thermal exhaust port. Luke Skywalker was there, his tiny spacecraft rocking and shaking, buffeted by explosions. As he closed in on his target, Luke did something truly daring—he switched off his targeting system. He was now relying solely on the Force to help him find his objective.
Exciting, right? Now, while this might be perfectly believable in George Lucas’s iconic Star Wars series, the Force simply isn’t strong enough in the real world to protect our enterprises from harm.
Unlike Luke Skywalker, we have to keep our eyes open and be aware of our surroundings. Visibility into what is happening on our assets and who is accessing our data is essential, and our newly released report—the Security Outcomes Study, Vol. 2—addresses this challenge directly. It also raises this big question: how exactly can enhanced visibility increase our chances of guarding against data breaches and attacks?
Here, in part four of our five-part blog series, we’ll be focusing on that very question.
People, processes, and technology: The cybersecurity trinity
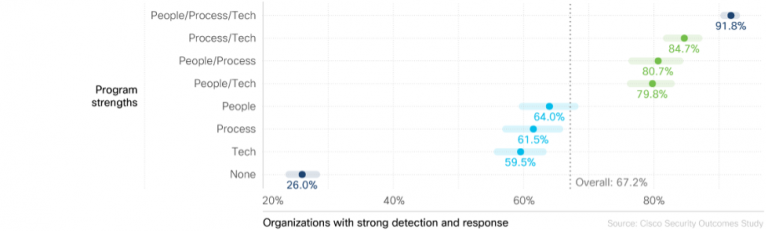
First off, we need to puzzle out how we gain accurate threat detection. It’s hard to defend the enterprise when there is no clear understanding of the threats laid out before you! To do that, we must concentrate on the three core tenets of any security program: people, processes, and technology.
Had the Empire known of the threats the Rebels posed, they could have mounted a stronger defense. The Rebels were able to protect their own people thanks to technology—good intelligence—that helped them counter the threat.
When a security program gained strength in any one of these areas—people, process, or technology—they were able to boost the confidence in their SecOps, all the way up to 60 or 64%, depending on the findings in the Security Outcomes Study, Vol. 2.

Automate to protect
But is there any particular part of the aforementioned triad that is more critical than the others? Well, in a manner of speaking, yes. The study found that organizations that used threat intelligence extensively were almost twice as likely to report a strong threat detection capability.
In addition, the study noted that enterprises using threat intelligence information more extensively managed to cut in half their mean time recovery from attacks. This is all well and good, but we should keep in mind that a full third of all the companies polled for the study did not have a strong security team or defined repeatable processes.

When companies automate threat monitoring, event analysis, or incident response, their numbers jump significantly for threat detection. These numbers would rise even higher with the automation of a second aspect. Over one-third of SecOps programs built a more robust security practice through automation, despite not having strong security staff available.
So, how do we get to a better place where those vulnerabilities are not so vexing? First and foremost, enterprises need to improve testing and actively update detection rules and use cases. There is a clear need for defenders to proactively hunt for signs of malicious activity on their assets and resources and to never assume that all is well.
Don’t forget the human element
While automation can help any security practice, one must not discount the human element. It is still essential to engage in red team and purple team exercises. In doing so, your enterprise will build muscle memory that will be priceless in the event of a breach or attack, all while tightening up that Mean Time to Detect (MTTR).
Whether you are countering an adversary or defending an enterprise, the need to have accurate threat detection cannot be overstated. If you are lucky enough to have a strong security team, that’s fantastic. If there’s a chance to augment that team with automation of threat detection and technology, that’s even better. The defenders can concentrate more effectively, and this will lead to more concise usage of available resources.
Ultimately, the Empire would have been well-served to have accurate threat detection in their environment, which could have helped them avoid the exact same exposure—in one form or another— through three different movies. Thankfully, at least in a galaxy far, far away, they didn’t.
The makings of a great cybersecurity program
Accurate threat detection is just one major tool in the SecOps toolbox that will elevate any cybersecurity program. In the Security Outcomes Study, Vol. 2, we honed in on five key tools—accurate threat detection, being one of them—that can lead to the greatest cybersecurity outcomes for any organization.
Interested in hearing more? Read blog posts from my other colleagues, highlighting each of these critical components. And consider downloading the full report to see insights from over 5,700 security professionals across the globe.
And, of course, happy hunting!
We’d love to hear what you think. Ask a Question, Comment Below, and Stay Connected with Cisco Secure on social!
Cisco Secure Social Channels

