Salfram: Robbing the place without removing your name tag
September 3, 2020
Homegrown Tech Enabler: Enfrasys Drives Malaysian Organizations’ Digitally Forward
September 4, 2020Threat protection: The WastedLocker ransomware
Co-authored by Martin Lee, Talos Outreach manager, EMEA.
Threat Protection is a new blog series as part of a collaboration between Talos and Cisco Security, combining Talos’ knowledge of the threat landscape and the Cisco Security portfolio. In it, we will highlight particular threats and showcase how Cisco Security’s multi-layered approach can prevent them from affecting your network.
WastedLocker is a ransomware family that threat actors continue to use in targeted attacks. Cisco Talos originally wrote about this ransomware family in early July, though attacks have continued since publication.
The threat actors behind the ransomware family appear to target specific organizations rather than individuals. Once the attacker obtains a foothold, they spread across the network using dual use tools and living-off-the-land binaries (aka LoLBins) to further compromise additional systems. When key systems are under control of the attackers, they execute the ransomware payload. This cripples the victim, increasing the likelihood the targeted organization will consider paying the ransom demanded.
Threat delivery
One of the primary mechanisms used to infect users is compromising legitimate websites. Many of the attackers who have compromised these sites are utilizing a malware delivery framework called SocGholish, which can be used to display fake web pages and deliver malware payloads. If a user visits one of these pages, it displays a fake alert informing the user that their browser is out of date and instructs them to download an update. If the user clicks the prompt, malicious code is downloaded.
Cisco Umbrella can prevent access to these malicious sites. Umbrella keeps track of compromised websites that serve malware, and the supporting infrastructure of malicious websites, blocking access to these sites at the DNS level. This prevents users from being exposed to the malicious prompts or downloading fake browser extensions.
If a user attempts to visit one of these malicious sites, an alert will be generated by Umbrella, allowing an analyst from the security operations center (SOC), or similar team, to further investigate. Using Umbrella Investigate, the analyst can look up additional information on the domain.

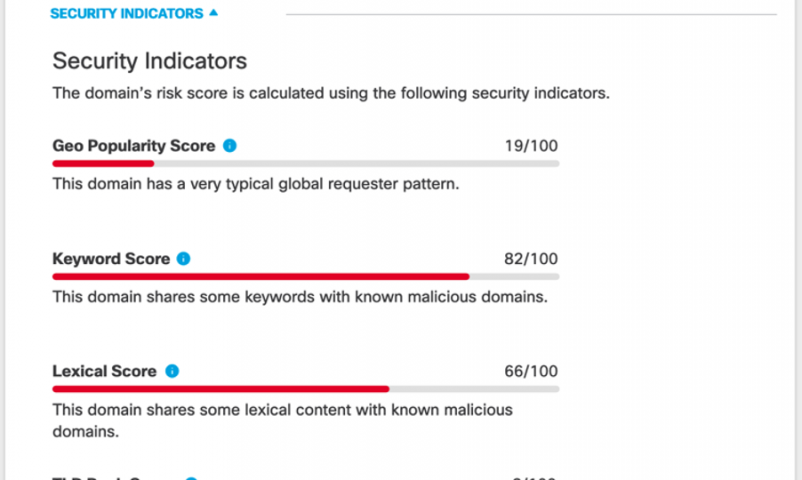
Not only does Investigate show that the malicious site has a history of serving up malicious code, having previously been associated with SmokeLoader, but the high keyword and lexical scores in the overall Domain Risk Score provide details as to why Umbrella blocked this site—even if it wasn’t serving up malicious code at that moment, its structure is highly suspect.
Initial infection
Assuming that DNS protections such as Umbrella aren’t in place, and the user visits one of these pages, they are presented with a fake notification that their browser is out of date. However, the .zip file that they are prompted to download is malicious.
Fortunately, AMP for Endpoints can stop the payload SocGholish delivers, as evidenced by the following screenshot from Cisco SecureX threat response. In this case, an AMP File Reputation module stops the .zip file due to a malicious disposition and a “high” severity rating. The file is also flagged by the AMP Global Intelligence module thanks to AMP’s integration with Cisco Threat Grid.

It turns out that this file had previously been sent to Cisco Threat Grid for analysis. If a SOC analyst wishes to investigate to see what the file may do, they can pivot to Cisco Threat Grid and have a look. Doing so shows some of the features that can be detected both by static and dynamic analysis as the code executes.

In this case, the indicators show several suspicious things about the file:
- It has been flagged by multiple antivirus services.
- It communicated with a domain on Umbrella’s block list.
- It uploaded a file to a malicious domain.
- It deleted the original file sample.
All these behaviors contribute to the conclusion that this is a malicious file.
Establishing a foothold
Assuming they are successful in getting a user to download the malicious .zip file and launching the initial payload, the attackers behind WastedLocker often use multiple tools at this stage—some malicious, some dual-use—to extend their penetration into the organization.
For instance, the threat actors often leverage Cobalt Strike to move laterally between systems across the network. They use these tools to execute commands, escalate privileges, and perform process injection and/or impersonation on compromised computers. The attackers also often dump login credentials to gain access to other systems on the network.
AMP for Endpoints can detect malicious activity where dual-use tools may have been utilized on endpoints. But beyond the endpoint, both Cisco Stealthwatch and Cisco Firewalls with AMP for Networks allow security teams to identify when attackers attempt to utilize them to move laterally across the network. Cisco SecureX also provides a single view, combining the findings of various security tools into one view, so that the subtle ways that threat actors expand their presence can be identified more easily, and sooner.
The ransomware payload
Once key systems have been compromised, the threat actors deploy the WastedLocker payload. The payload is characteristic of ransomware: It encrypts files on the computer, using a file extension that includes the string “wasted,” and deletes any shadow copy backups of files.
Even if the malware is customized for a target, there are still many functions that the malware must execute to fulfil its goals. This activity allows us to detect ransomware in Cisco Threat Grid and push that detection in AMP, even if the ransomware variant is unique.
By having a sample or hash to hand, an analyst can submit it to Cisco Threat Grid for further analysis. In the resulting report, the File Activity section clearly shows the ransomware encrypting files with the characteristic file extension (in this case “.bbawasted_info”) within Cisco Threat Grid’s sandbox environment.

In this case, the ransomware shares similarities to an older ransomware family, BitPaymer. It is not unusual to encounter situations like this, as there are only so many ways to encrypt files. On the positive side, reused techniques such as these often help facilitate detection. Deleting backups and shadow copies are two other techniques frequently used by ransomware. Hence, we can detect new types of ransomware that carry out the same old tricks

Conclusion
Well-planned and executed ransomware attacks can be devastating. The good news is that there are plenty of things that can be done to reduce the chances that these attacks are successful.
As we walked through this infection path for the WastedLocker ransomware, we’ve demonstrated how Cisco Security products can detect multiple stages of the attack and prevent it from reaching its intended goal of holding the network for ransom.
But the real power here is brought forth when these products are combined, and Cisco SecureX can do just that, bringing seemingly disparate products together into one place. This is the true strength of Cisco SecureX—a cyber security platform that can be leveraged to cover your entire infrastructure using an integrated, open platform, combining the following to block threats like WastedLocker:
- Cisco Umbrella to block connections to malicious domains used in the initiation of attacks, and in command and control (C2) activities.
- AMP for Endpoints to detect and block the malicious code used to initiate attacks, expand the attackers’ presence, and encrypt systems.
- Cisco Threat Grid to sandbox suspicious files and learn more about their behavior.
- Cisco Stealthwatch to detect and prevent the lateral movement of threat actors within your network.
- Cisco Firewalls with AMP for Networks to detect malicious code being transferred between systems over networks.
- Cisco SecureX threat response to provide the visibility and context that allows security teams to detect and respond to malicious incursions sooner.
It’s also important to ensure that security teams back up data and systems to an offline location. Defenders should regularly check the integrity of those backups to ensure that they can be restored. That way, if faced with a worst-case scenario, victims can recover their data, rather than paying the ransom.
Cisco Talos Incident Response can aid organizations to help respond to active attacks, or in recovery after attacks. Talos Incident Response provides an innovative approach, capitalizing on our unmatched visibility, unique and actionable threat intelligence, and collective, global response capability, together in a full-spectrum offer.
The post Threat protection: The WastedLocker ransomware appeared first on Cisco Blogs.

