The million-dollar question: Is Cisco SecureX the same as XDR?
September 22, 2020
Are you ready to place a call for simplified cybersecurity? It’s time to stop switchboarding.
September 22, 2020Why Endpoint Security Matters in Protecting Remote Workers – Part 2
As attack surfaces expand customers see improved visibility with AMP for Endpoints!
In part 1 of this blog series we discussed how securing your workforce on any endpoint, anywhere, at any time, is more important now than ever before, and that Cisco AMP for Endpoints plays a critical role in the new Cisco Secure Remote Worker solution that connects and protects people and devices working remotely.
In the first entry of this blog series we promised to take a more in-depth look at our customer’s thoughts on the value that AMP for Endpoints brings to their business. As a quick recap the Top 3 business values from that Endpoint survey are:
- Better visibility – for insights and protection to stop threats from the expanding attack surface
- Better efficacy – to remediate faster and fully expose, contain and resolve threats
- Getting time back – for improved security effectiveness, eliminating complexity and enhancing security admin productivity
Now in part 2 of this series let’s take a look at the first of the top three business values – visibility.
Business Value #1: Better visibility into endpoints
The customer challenge: Customers tell us that their endpoints are under constant attack through phishing attempts, advanced persistent threats (APTs) and exploits. One of the key needs to defend their networks is to arm teams with better visibility and actionable insights. And with recent events coupled with the new reality of securing remote workers, we are hearing; “…endpoints are moving, more and more, out of the office now …we use Cisco AMP and Umbrella on those endpoints to secure them and to deliver consistent policy.”
Visibility described: A bit of a definition is in order. The short answer is that visibility provides security practitioners the ability to see threat status, indicators and timelines on endpoints (as well as the files) on a summary basis or individually. There are other ways to describe visibility, but as our AMP for Endpoint customers like to say, “we can see everything that’s going on in our endpoints.” And that is very valuable.
Why it’s important: As mentioned in the first blog, if you don’t have visibility into your endpoints you really don’t know if malware is present or where it came from. Consequently, your team could waste valuable time attempting to eradicate low priority threats or have threats go undetected, all the while your infrastructure could be at risk from potential malware lateral movement. Our customers have noticed the benefits after deploying AMP for Endpoints, as one mentions; “It has decreased time to detection by 95%. A lot of the time, prior to having AMP, …we weren’t aware of any type of malicious activity until it had an impact on the organization.”
Now let’s take a look at three examples of visibility; (1) a high-level view of endpoint security through the dashboard, and (2) a drill down of events that occurred on a specific endpoint that we call device trajectory, and last but not least, (3) a snapshot view from Orbital, our Advanced Search feature.
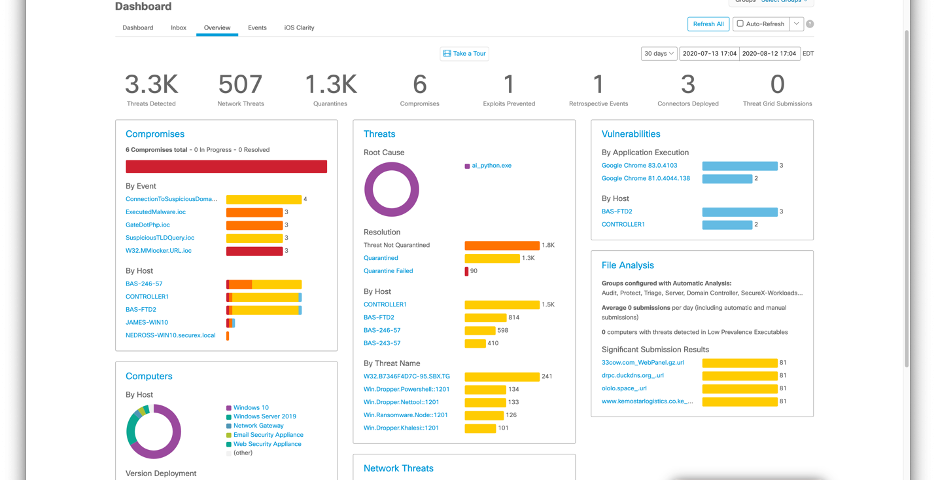
Dashboard view: The AMP for Endpoints dashboard view provides an instantaneous real-time snapshot of key aspects such as Compromises, Threats and Vulnerabilities. The key objective is to help the security team understand activities on the endpoint and help determine priorities. It provides a quick view of many other aspects while enabling a single mouse click to find out more, right from the dashboard. A common customer feedback we hear is, “For the endpoint, Cisco gives us good clarity about what our endpoints are actually doing. So when we get bad actors into the network, we get quick visibility into which devices are compromised.”

Device Trajectory: Unlike the dashboard view which provides a global summary of endpoint activity, tools like file trajectory, and in the case of device trajectory depicted in figure 2 below, use AMP’s continuous analysis capabilities to show your security team the full scope of a threat. AMP identifies all affected applications, processes, and systems to pinpoint threats such as patient zero, as well as the method and point of entry. These capabilities help your team quickly see and understand the scope of the problem by identifying malware gateways and the path that attackers are using to gain a foothold into other systems. Thus, in a customer’s words, “If malware has infected a certain laptop, we get all the forensic evidence around that laptop and, if it’s jumped, where that bad stuff has jumped to and what it’s done. All that visibility is possible because of AMP for Endpoints.”

Forensic Snapshots with Orbital Advanced Search: Especially helpful for threat hunters, we can capture a forensic snapshot of data from an endpoint such as running processes, open network ports and a lot more at the time of detection or on demand. You can think about it as a “freeze framing activity” on an endpoint right to the moment when something malicious was seen. This allows you to know exactly what was happening on your endpoint at that point in time. It’s big on giving you time back! One of our customers, a security consultant, explains it this way, “…Orbital is saving us five to eight hours per incident. In one week, it could save eight hours, and then another week, it could save 32 hours.”

Wait! There’s more: With AMP for Endpoints, you have access to our built-in SecureX platform, providing integration with other Cisco security technologies and a wide range of third-party products, backed by Talos threat intelligence, to help you block, detect, investigate, and respond to threats across your entire environment – not just at your endpoints.
One of our customer notes that; “This solution interfaces with Talos Intelligence, Threat Grid, SecureX Threat Response and the SecureX (platform). All of these products are integrating together and a lot of security is now starting to happen automatically…”
For the next entry in this series
In the next blog entry of this series we will dive into the second of the three business values (better efficacy) and demonstrate how our customers are getting the results they need.
In the meantime, please visit the TechValidate Survey and IT Central Station reviews to see examples of what our customer’s challenges were, and in their own words, express how they were able to achieve their business goals with Cisco AMP for Endpoints as part of the Cisco SecureX platform.
The post Why Endpoint Security Matters in Protecting Remote Workers – Part 2 appeared first on Cisco Blogs.

