
Gain WiFi Performance Advantages Over Your Competition
September 26, 2020
Threat Roundup for September 18 to September 25
September 27, 2020Zero Trust in a COVID-19 remote world
By Dr Dzahar Mansor, National Technology Officer, Microsoft Malaysia
Millions across the world have made the transition to remote working in past months, and this massive migration has challenged advanced security models and user behaviors in a COVID-19 world. In Asia Pacific, Gartner reported that an estimated 91% of organizations have adopted work from home arrangements since the outbreak, with 54% indicating that poor technology and/or infrastructure was the biggest barrier to effective remote working.
As the world progresses towards the new normal of hybrid workplaces, organizations in Asia are now taking stock of their business continuity measures and addressing the pressing needs that can restore productivity levels in the near to long-term. A big part of this effort is ensuring that they have the right technological infrastructure and tools for their employees as well as the best practices in place like modern cyber hygiene controls.
Closer to home, with more Malaysians working in remote or hybrid arrangements, we saw an increase of COVID-19 themed attacks in Malaysia since the pandemic. Additionally, statistics from the Ministry of Communications and Multimedia revealed that incidents involving cybersecurity have increased by 109 percent since the outbreak. Meanwhile, CyberSecurity Malaysia reported that during the first few weeks of MCO between March 18 and April 7, there was an 82.5 percent increase compared to the same time frame last year.
This reinforces the importance of dealing more intelligently with cybersecurity threats is crucial in this new normal. From Microsoft’s data, cybercriminals have been taking advantage of the global pandemic by adapting and updating their attack methods to capitalizes on peoples’ fears, and users who click on these malicious links can be vulnerable to identity theft.
The good news is that cyberattack risks can be minimized through Zero Trust security : an organizational process and perspective that takes precautions on security every step of the way, as if the organization is being accessed by a stranger each time.
Enabling safer work from home processes effectively means transitioning existing network infrastructure and capabilities into a Zero Trust security framework. Most organizations are already moving toward this goal and it is anticipated that they will accelerate this transition in the coming months.
What is and why Zero Trust?
“Never trust, always verify”, is the bedrock of Zero Trust.
The use of digital technologies such as personal mobile devices and hyperscale cloud assets have become an integral part of modern business. Hence, corporations need to adopt a consistent cyber security strategy that extends beyond their on-premises network boundaries. The Zero Trust model assumes breach and verifies every access request as though it originates from an open network – regardless of where the request originates (internal or external to the enterprise network boundaries) or what resource it accesses. With this model, every data access request is fully authenticated, authorized, and encrypted before it is granted. Across identities, devices, applications, data, infrastructure and the network, the Zero Trust strategy involves always verifying this access explicitly, always using least privileged access and always assuming breach. It empowers organizations to limit access to specific apps and resources only to the authorized users who can access them.
This model has become especially important given that cybercriminals are here to stay, even as they evolve their tactics, with or without COVID-19.
Securing flexible work going forward
For companies which already have proof of concept underway for their Zero Trust journey, COVID-19 served as an accelerator, moving up the timelines for digital adoption. The ability to separate application access from network access, and secure application access based on identity and user context, such as date/time, geolocation, and device posture, was critical for IT departments’ ability to enable remote work.
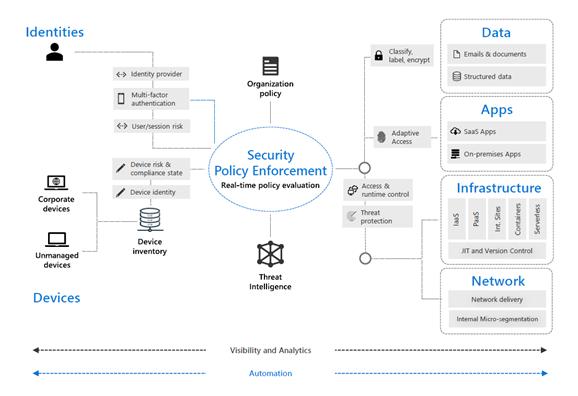
In rethinking cybersecurity strategy, organizations can evolve beyond traditional security controls to implement Zero Trust across six key pillars:
- Identities – whether representing people, services or IoT devices, these are where the attempt to access a resource will originate from and need to be verified.
- Devices – IoT devices to smartphones, BYODs to partner managed devices, on-premise workloads to cloud hosted servers, where data can seamlessly flow when access is granted.
- Applications – providers of the interface through which data is consumed.
- Data – the asset that security teams are focused on protecting; these should be classified, labeled, and encrypted, with access restricted where needed.
- Infrastructure – represents a critical threat vector, which is the path/means by which a cybercriminal may gain access.
- Networks – where all data is ultimately accessed over; these should be segmented with real-time threat protection, end-to-end encryption, monitoring and analytics, to prevent lateral movements by attackers.
Across the digital estate, the below illustrates how all of these components work together in a Zero Trust model.
Tools that drive Zero Trust
Organizations across Asia would be at different stages of their Zero Trust journey, and understanding an organization’s maturity level could help bring it closer to optimal adoption. Some of the key attributes of robust Zero Trust implementation includes:
- Strong authentication – using multi factor authentication (MFA) and session risk detection as the backbone of access strategy to minimize the risk of identity compromise.
- Policy-based adaptive access – involving defining acceptable access policies for resources and enforcing them with a consistent security policy engine that provides both governance and insight into variances.
- Micro segmentation – moving beyond a simple centralized network to comprehensive and distributed segmentation of networks with micro-perimeters.
- Automation – investing in automated alerting and remediation, to reduce an organization’s mean time to respond (MTTR) to attacks.
- Intelligence and AI – utilizing cloud intelligence and all available signals to detect and respond to access anomalies in real time.
- Data classification and protection – discovering, classifying, protecting, and monitoring sensitive data to minimize exposure from malicious or accidental exfiltration.

Future-proofing cybersecurity
Cybersecurity is now an enabler for business, and reliance on internet enable digital technologies is not an option. Zero Trust is a modern cybersecurity paradigm where no implicit trust is granted based solely on the physical and network location or device ownership that not only enhances the security posture of organizations, but enables seamless and secure remote access. Progressively, a phased approach in-line with resources and priorities can allow organizations to move toward higher levels of security.
Ultimately, people are at the forefront of any successful organization, and safe technology is here to enable. Zero-trust advancement comes hand-in-hand with empowering employees to work when, where, and how they need to, using the devices and apps they find most useful. It is the foundation of a future-ready workforce here in Asia.
The post Zero Trust in a COVID-19 remote world appeared first on Microsoft Malaysia News Center.

